Encrypting hard drives should be a common step in our regular computer
usage. If nothing else, this will help you sleep well, in case you
lose your computer (theft) or that small USB disk you were carrying in
your pocket. In this guide, I’ll explain how to encrypt your USB
disks so that you have peace of mind, in case you lose them.
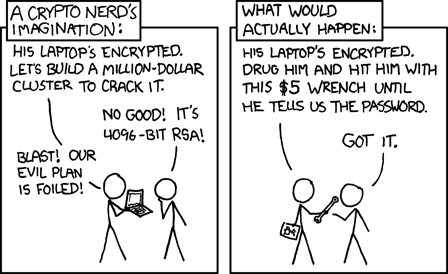
But, before we dig into the technical details, always remember the
following from XKCD.
What is LUKS?
LUKS or Linux Unified Key
Setup is a disk encryption
specification, first introduced in 2004 by Clemens Fruhwirth.
Notice the word specification; instead of trying to implement
something of its own, LUKS is a standard way of doing drive encryption
across tools and distributions. You can even use drives from Windows
using the LibreCrypt
application.
For the following example, I am going to use a standard 16 GB USB
stick as my external drive.
Formatting the drive
Note: check the drive name/path twice before you press enter for any
of the commands below. A mistake, might destroy your primary drive,
and there is no way to recover the data. So, execute with
caution.
In my case, the drive is detected as /dev/sdb.
It is always a good idea to format the drive before you start using it.
You can use wipefs tool to clean any signature from the device,
$ sudo wipefs -a /dev/sdb1
Then you can use fdisk tool
to delete the old partitions , and create a new primary partition.
Next step is to create the LUKS partition.
$ sudo cryptsetup luksFormat /dev/sdb1
WARNING!
========
This will overwrite data on /dev/sdb1 irrevocably.
Are you sure? (Type uppercase yes): YES
Enter passphrase:
Verify passphrase:
Opening up the encrypted drive and creating a filesystem
Next, we will open up the drive using the passphrase we just gave, and
create a filesystem on the device.
$ sudo cryptsetup luksOpen /dev/sdb1 reddrive
Enter passphrase for /dev/sdb1
$ ls -l /dev/mapper/reddrive
lrwxrwxrwx. 1 root root 7 Jul 17 10:18 /dev/mapper/reddrive -> ../dm-5
I am going to create an EXT4 filesystem on here.
Feel free to create which ever filesystem you want.
$ sudo mkfs.ext4 /dev/mapper/reddrive -L reddrive
mke2fs 1.43.4 (31-Jan-2017)
Creating filesystem with 3815424 4k blocks and 954720 inodes
Filesystem UUID: b00be39d-4656-4022-92ea-6a518b08f1e1
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632, 2654208
Allocating group tables: done
Writing inode tables: done
Creating journal (16384 blocks): done
Writing superblocks and filesystem accounting information: done
Mounting, using, and unmounting the drive
The device is now ready to use. You can manually mount it with the
mount command. Any of the modern desktops will ask you to unlock
using the passphrase if you connect the device (or try to double click
on the file browser).
I will show the command line option. I will create a file hello.txt as an example.
$ sudo mount /dev/mapper/reddrive /mnt/red
$ su -c "echo hello > /mnt/red/hello.txt"
Password:
$ ls -l /mnt/red
total 20
-rw-rw-r--. 1 root root 6 Jul 17 10:26 hello.txt
drwx------. 2 root root 16384 Jul 17 10:21 lost+found
$ sudo umount /mnt/red
$ sudo cryptsetup luksClose reddrive
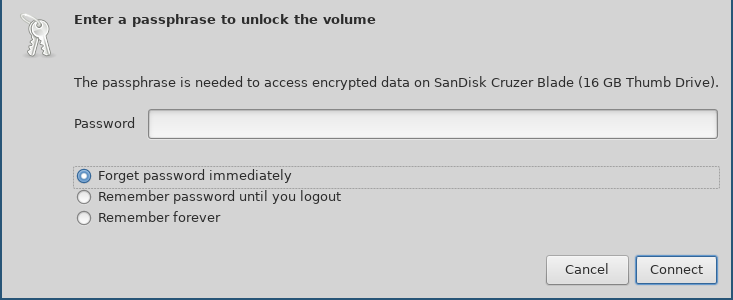
When I attach the drive to my system, the file browser asks me to
unlock it using the following dialog. Remember to choose forget
immediately so that the file browser forgets the password.
On passphrases
The FAQ
entry
on cryptsetup page, give us hints and suggestions about passphrase
creation.
If paranoid, add at least 20 bit. That is roughly four additional
characters for random passphrases and roughly 32 characters for a
random English sentence.
Key slots aka different passphrases
In LUKS, we get 8 different key slots (for passphrases) for each
device(partition). You can see them using luksDump sub-command.
$ sudo cryptsetup luksDump /dev/sdb1 | grep Slot
Key Slot 0: ENABLED
Key Slot 1: DISABLED
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
Adding a new key
The following command adds a new key to the drive.
$ sudo cryptsetup luksAddKey /dev/sdb1 -S 5
Enter any existing passphrase:
Enter new passphrase for key slot:
Verify passphrase:
You will have to use any of the existing passphrases to add a new key.
$ sudo cryptsetup luksDump /dev/sdb1 | grep Slot
Key Slot 0: ENABLED
Key Slot 1: DISABLED
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: ENABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
Removing a passphrase
Remember that removing a passphrase is based on the passphrase
itself, not by the key slot number.
$ sudo cryptsetup luksRemoveKey /dev/sdb1
Enter passphrase to be deleted:
$ sudo cryptsetup luksDump /dev/sdb1 | grep Slot
Key Slot 0: ENABLED
Key Slot 1: DISABLED
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
Now in case you don't know the passphrase, then you can use
luksKillSlot.
$ sudo cryptsetup luksKillSlot /dev/sdb1 3
Enter any remaining passphrase:
Overview of the disk layout
The disk layout looks like the following. The header or phdr contains
various details like magic value, version, cipher name, following the
8 keyblocks (marked as kb1, kb2.. in the drawing), and then the
encrypted bulk data block. We can see all of those details in the C
structure.

struct luks_phdr {
char magic[LUKS_MAGIC_L];
uint16_t version;
char cipherName[LUKS_CIPHERNAME_L];
char cipherMode[LUKS_CIPHERMODE_L];
char hashSpec[LUKS_HASHSPEC_L];
uint32_t payloadOffset;
uint32_t keyBytes;
char mkDigest[LUKS_DIGESTSIZE];
char mkDigestSalt[LUKS_SALTSIZE];
uint32_t mkDigestIterations;
char uuid[UUID_STRING_L];
struct {
uint32_t active;
/* parameters used for password processing */
uint32_t passwordIterations;
char passwordSalt[LUKS_SALTSIZE];
/* parameters used for AF store/load */
uint32_t keyMaterialOffset;
uint32_t stripes;
} keyblock[LUKS_NUMKEYS];
/* Align it to 512 sector size */
char _padding[432];
};
Each (active) keyblock contains an encrypted copy of the master
key. When we enter the passphrase, it unlocks the master key, that in
turn unlocks the encrypted data.
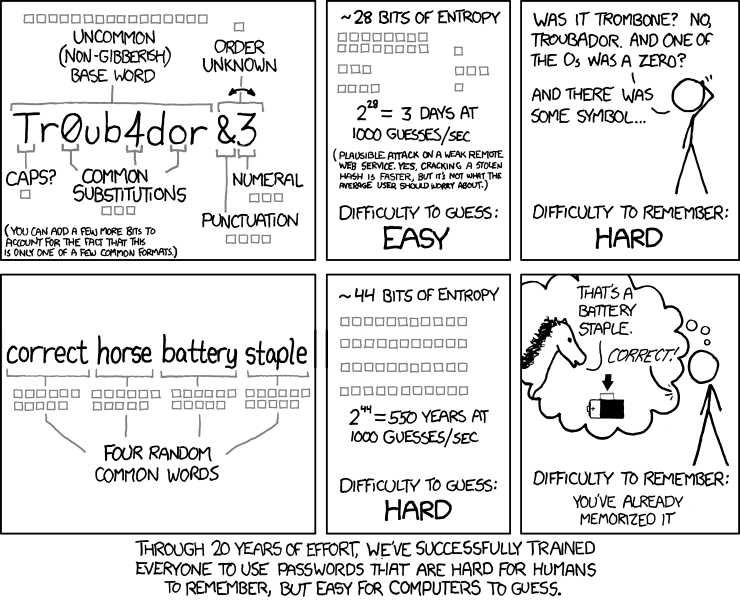
But, remember, all of this is of no use if you have a very simple
passphrase. We have another XKCD to
explain this.
I hope this post encourages you to use encrypted drives more. All of
my computers have their drives encrypted; (I do that while installing
the Operating System.) This means, without decrypting the drive you
can not boot the system properly. On a related note, remember to turn
off your computer completely, (not hibernation or suspend mode) when
you’re traveling.