IP addresses which tried to break into this server in 2019
This Friday, I tried to look into the SSH failures on my servers, how different systems/bots/people tried to break into the servers. I have the logs from July this month (when I moved into newer servers).
Following the standard trends, most of the IP addresses are working as a staging area for attacks by other malware or people. Most of these IP addresses are the real people/places from where the attacks are originating. There are around 2.3k+ IP addresses in this list.
Origin IP locations
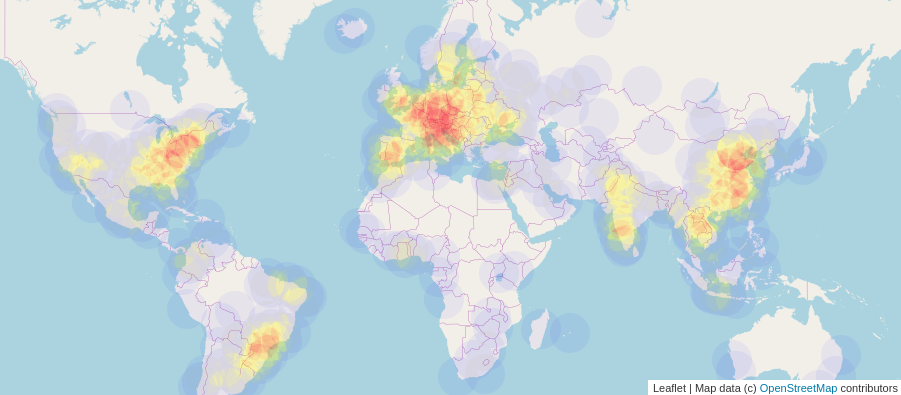
The above is a map of all of the IP addresses which tried to break into my system.
Country wise
You can see there is a big RED circle here, as one particular IP from Belgium tried 3k+ times, the second country is China, and the USA is in third place. I made the map into a static image as that is easier for the page load.
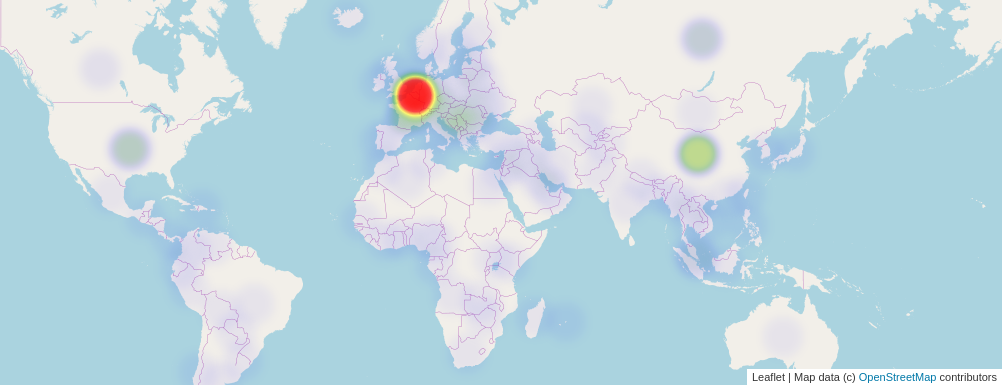
BE 3032
CN 1577
US 978
FR 934
RU 807
SG 483
DE 405
NL 319
CA 279
KR 276
Known VS unknown IP addresses
I also verified the IP addresses against AlienVault database, and it is an open threat intelligence community. The API is very simple to use.
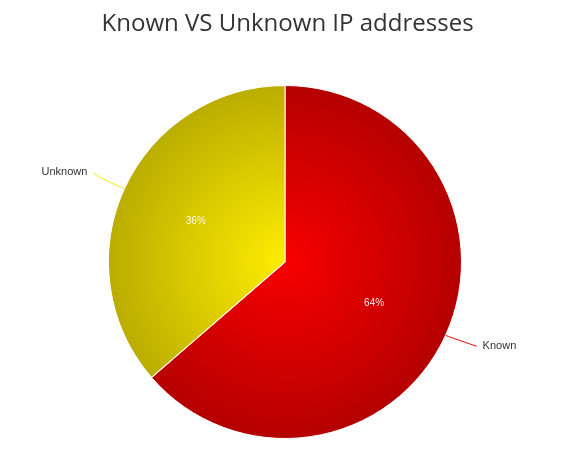
According to the AlienVault, 1513 IP addresses are already known for similar kinds of attacks, and 864 IP addresses are unknown. In the coming days, I will submit back these IP addresses to AlienVault.
I took the highest amount of time to learn how to do that heatmap on the world map. I will write a separate blog post on that topic.