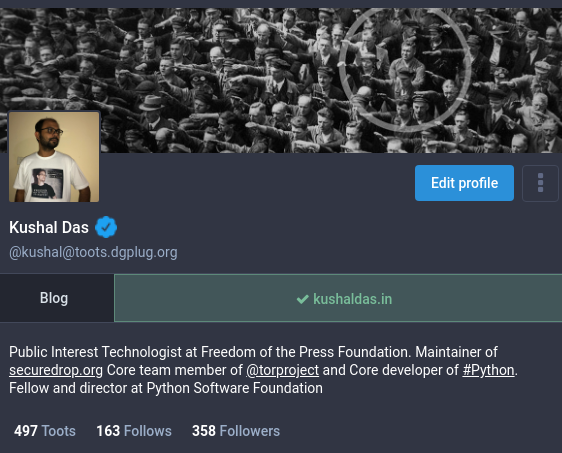
Indian police attacked university campuses on government order

Yesterday, Indian police attacked protesting students across different university campuses. They fired tear gas shells inside of libraries; they lit buses on fire and then told that the students did it. They broke into a Mosque and beat up students there.
The Internet has been shut down in Kashmir for over 130 days, and now few more states + different smaller parts of the country are having the same.
Search for #JamiaProtest or #SOSJamia on twitter to see what is going on in India. I asked to my around 5k followers, to reply if they can see our tweets (only around 5 replied via the original tweet).
Trigger warning (The following tweets shows police brutality)
I have curated a few tweets for you, please see these (if possible) and then share those.
- Police + goons (posing as police) beating up the girls https://twitter.com/amirul_alig/status/1206273340194746368
- Police attacked the library where students were studying https://twitter.com/i_kathayat/status/1206271022976008194
- Police attacking Jamia Milia University library https://twitter.com/imMAK02/status/1206213159981203458
- Police vandalizing university https://twitter.com/amirul_alig/status/1206273340194746368
- Police firing tear gases at AMU https://twitter.com/imMAK02/status/1206244102641049600
- Police firing their guns https://twitter.com/imMAK02/status/1206233908083187712
- Police vandalizing public property https://twitter.com/imMAK02/status/1206259162969038848
- Police breaking the gate of Aligarh Muslim University https://twitter.com/imMAK02/status/1206261850943311873
- Police putting fire on a bus https://twitter.com/DesiPoliticks/status/1206222796927438848
- Police attacking AMU https://twitter.com/tariq_shameem/status/1206259086796279810
Why am I writing this in my blog (maybe you are reading it on a technical planet)?
Most people are ignorant about the fascist regime in India, and the IT industry (including us) mostly tries to pretend that everything is perfect. I hope at least a few more around will read the tweets linked from this post and also watch the videos. I hope you will share those in your social circles. To stop fascists, we have to rise together.
Btw, you should at least read this story from New Yorker on how the fascist government is attacking the fellow citizens.
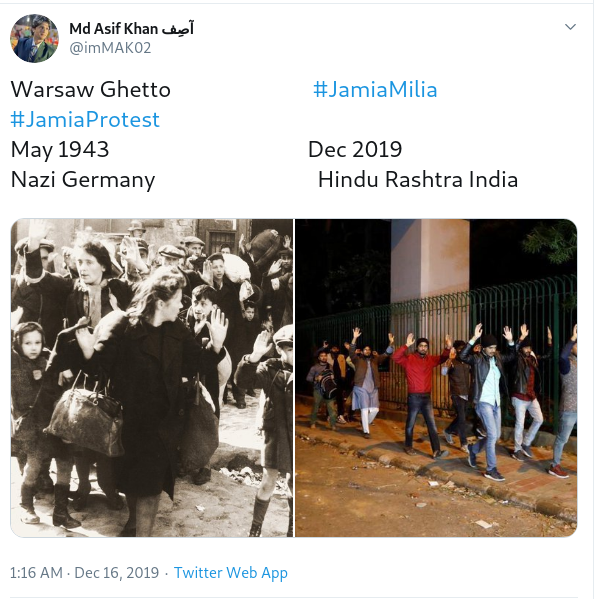
To know about the reason behind the current protest, read this story showing the similarities between Nazi Germany and current Indian government.
Top most drawing credit: I am yet to find the original artist, I will update when I find the name.