Get a TLS certificate for your onion service
For a long time, I wanted to have a certificate for the onion address of my blog. Digicert was the only CA who was providing those certificates with an Extended Validation. Those are costly and suitable for an organization to get, but not for me personally, especially due to the cost.
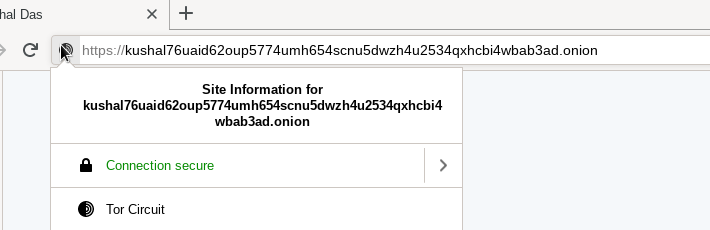
A few days ago, on IRC, I found out that Harica is providing Domain validation for the onion sites for around €30 per year. I jumped in to get one. At the same time, ahf was also getting his certificate. He helped me with the configuration for nginx.
How to get your own certificate?
- Make sure you have your site running as Tor v3 onion service
- Create an account at https://cm.harica.gr/
- Goto server certificates on the left bar, and make a new request for your domain, provide the onion address as requested in the form.
- It will give you the option to upload a CSR
Certificate Signing Request. You can generate one byopenssl req -newkey rsa:4096 -keyout kushaldas.in.onion.key -out csr.csr. For the common name, provide the same onion address. - After the click on the website, it will ask you to download a file and put it in your web root inside of
.well-known/pki-validation/directory. Make sure that you can access the file over Tor Browser. - When you click the final submission button, the system will take some time to verify the domain. After payment, you should be able to download the certificate with the full chain (the file ending with .p7b). There are 3 options on the webpage, so please remember to download the correct file :)
- You will have to convert it into PEM format, I used the command ahf showed me:
openssl pkcs7 -inform pem -in kushaldas.in.p7b -print_certs -out kushaldas.in.onion.chain.pem -outform pem
Setting up nginx
This part will be the same as any other standard nginx configuration. The following is what I use. Please uncomment
the Strict-Transport-Security header line only after you are sure everything is working fine.
server {
listen unix:/var/run/tor-hs-kushal.sock;
server_name kushal76uaid62oup5774umh654scnu5dwzh4u2534qxhcbi4wbab3ad.onion;
access_log /var/log/nginx/kushal_onion-access.log;
location / {
return 301 https://$host$request_uri;
}
}
server {
listen unix:/var/run/tor-hs-kushal-https.sock ssl http2;
server_name kushal76uaid62oup5774umh654scnu5dwzh4u2534qxhcbi4wbab3ad.onion;
access_log /var/log/nginx/kushal_onion-access.log;
ssl_certificate /etc/pki/kushaldas.in.onion.chain.pem;
ssl_certificate_key /etc/pki/kushaldas.in.onion.open.key;
#add_header Strict-Transport-Security "max-age=63072000; includeSubdomains";
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
# Turn on OCSP stapling as recommended at
# https://community.letsencrypt.org/t/integration-guide/13123
# requires nginx version >= 1.3.7
ssl_stapling on;
ssl_stapling_verify on;
# modern configuration. tweak to your needs.
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
index index.html;
root /var/www/kushaldas.in;
location / {
try_files $uri $uri/ =404;
}
}
I also have the following configuration in the /etc/tor/torrc file to use the unix socket files.
HiddenServiceDir /var/lib/tor/hs-kushal/
HiddenServiceVersion 3
HiddenServicePort 80 unix:/var/run/tor-hs-kushal-me.sock
HiddenServicePort 443 unix:/var/run/tor-hs-kushal-https.sock
In case you want to know more about why do you need the certificate for your onion address, the Tor Project has a very nice explanation.