Trouble with signing and notarization on macOS for Tumpa
This week I released the first version of Tumpa on Mac. Though the actual changes required for building the Mac app and dmg file were small, but I had to reap apart those few remaining hairs on my head to get it working on any other Mac (than the building box). It was the classic case of Works on my laptop.
The issue
Tumpa is a Python application which uses PySide2 and also Johnnycanencrypt which is written in Rust.
I tried both briefcase tool and
manual calling to codesign and create-dmg tools to create the tumpa.app
and the tumpa-0.1.3.dmg.
After creating the dmg file, I had to submit it for notarisation to Apple, following:
xcrun /Applications/Xcode.app/Contents/Developer/usr/bin/altool --notarize-app --primary-bundle-id "in.kushaldas.Tumpa" -u "kushaldas@gmail.com" -p "@keychain:MYNOTARIZATION" -f macOS/tumpa-0.1.3.dmg
This worked successfully, after a few minutes I can see that the job passed. So, I can then staple the ticket on the dmg file.
xcrun stapler staple macOS/tumpa-0.1.3.dmg
I can install from the file, and run the application, sounds great.
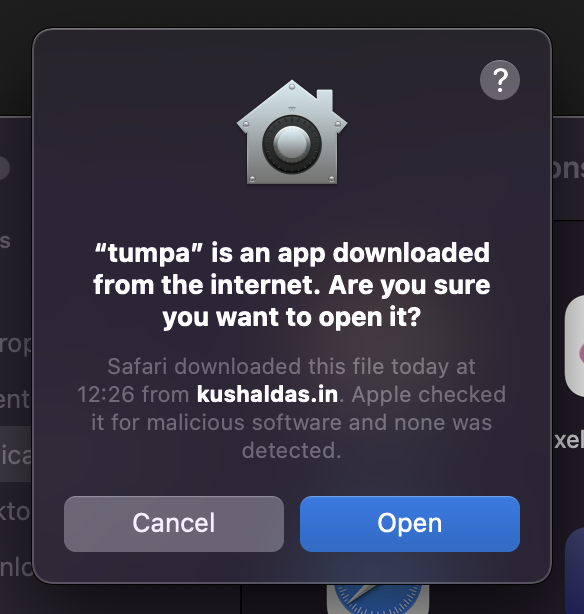
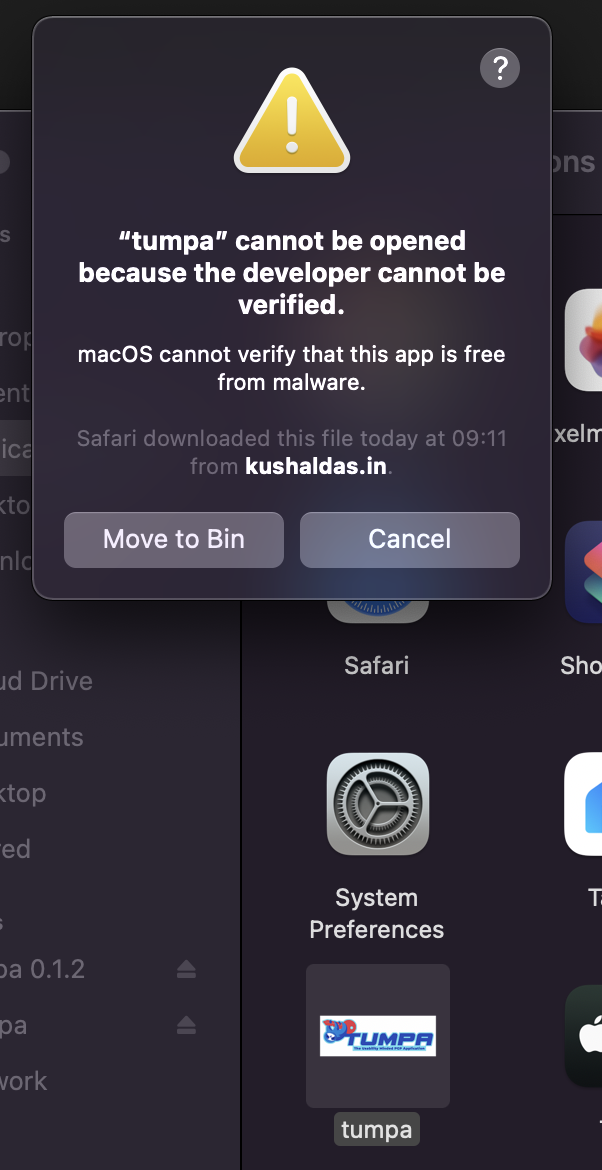
But, whenever someone else tried to run the application after installing from dmg, it showed the following.
Solution
It took me over 4 hours to keep trying all possible combinations, and finally I
had to pass --options=runtime,library to the codesign tool, and that did
the trick. Not being able to figure out how to get more logs on Mac was making
my life difficult.
I had to patch briefcase to make sure I can keep using it (also created the upstream issue).
--- .venv/lib/python3.9/site-packages/briefcase/platforms/macOS/__init__.py 2022-01-07 08:48:12.000000000 +0100
+++ /tmp/__init__.py 2022-01-07 08:47:54.000000000 +0100
@@ -117,7 +117,7 @@
'--deep', str(path),
'--force',
'--timestamp',
- '--options', 'runtime',
+ '--options', 'runtime,library',
],
check=True,
)
You can see my build script, which is based on input from Micah.
I want to thank all of my new friends inside of SUNET who were excellent helping hands to test the multiple builds of Tumpa. Later many folks from IRC also jumped in to help to test the tool.