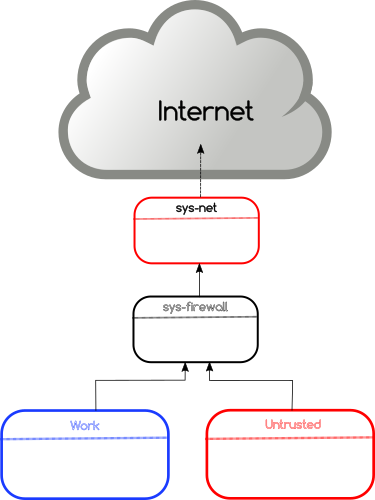
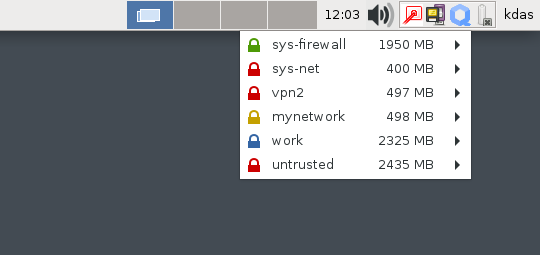
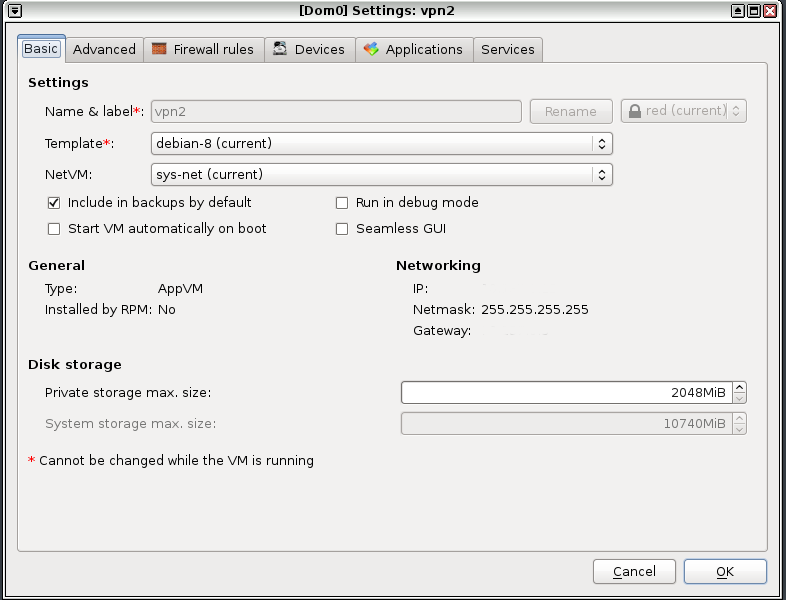
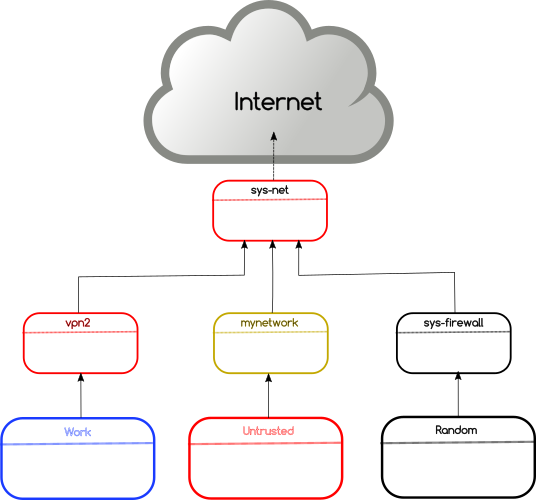
The journey continues at Freedom of the Press Foundation
The code we write is the extension of our emotions and thinking. A few months back a twitter thread on Gnome's account made Anwesha and me think about it once again. I think the most important reply in that thread came from Miguel de Icaza.
The contribution to Free Software happens over 2 forms, for many it helps to solve or support a personal cause. Sometimes it is something we deeply care about (actually the 2 points are not that different). That is why people come back to home from their daily jobs, and then continue contributing upstream till late night. Many jobs now also allow working on upstream Free Software projects as part of the work. The word Open Source helped to create a bridge between businesses and creators. But, we still have to keep fighting for Freedom in various levels in life, even including for the basic human rights.
More than a month back, the Supreme Court of India ruled that privacy is a fundamental right to every Indian citizen. It was a huge win for every privacy advocate, but it was one of the big battles in the whole fight for right to privacy. Even though governments are using public money to develop software infrastructure, almost none of them are Free Software. There is a current campaign happening for having publicly financed software developer for people to be Free Software. No one knows what is going on in the closed source infrastructure, and if people point out the issues, they are getting punished. If you never heard about Aadhaar project in India, feel free to visit this site to learn about how much destruction it is bringing in.
Journalists were the most common people in the movies (in our childhood days) who used to find out all bad things people in power were doing, and at the end of the movie, public used to win with help of court (and sometimes fights between the hero and villains). Things have changed a lot over the years. Now technology enables many to be in a condition to find out the wrongdoings of the state, or private companies. It is much easier to send across that information to the journalists, and we can see how those revelations are helping the world. But, technology also enables the wrong-doers to attack the whistleblowers and the journalists who publish the truth to the people.
At this point if the government can identify the whistleblower, it is too dangerous to be a whistleblower. If we want to find what the state is doing, so that, we, the people, can have control over it, we need to make whistleblowers safe. -- RMS in his talk last year.

Freedom of the Press Foundation is one such organization working to protect and defend journalism, to support journalists and whistleblowers worldwide. One of the major development from the foundation is SecureDrop project. SecureDrop is an open-source whistleblower submission system that media organizations can use to securely accept documents from and communicate with anonymous sources. It was originally created by the late Aaron Swartz. The project also won The Award for Projects of Social Benefit from Free Software Foundation in 2016. This week I joined the Freedom of the Press Foundation as a staff member to help on the SecureDrop and other projects.
As I started writing the post with Why Free Software?, helping the journalists and whistleblowers with Free Software is vital cause I can personally relate to. In the last month, we saw at least 3 journalists killed in India, from 1992, we have the second highest deaths of the journalists due to their work. We also saw the increased death threats to the journalists in India and other parts of the world. The freedom of the press stands as a pillar of the democracy, and we will continue to protect it.