From 5th August 2019, Kashmir is under a communication shutdown. SMS service
for a particular connection provider is now available for postpaid users, but
Internet is still down for all Indian citizens of Kashmir.
This is above 155 days of Internet shutdown. If you are reading this blog
post, it means you have an active Internet connection, and you can connect to
the different servers/services that are essential to modern life. Now, think
about all of those citizens of India staying in Kashmir. Think about the
problem when they have to access a website for job/medical/banking/travel or
any other necessary work.
The current fascist regime of India kept shouting about “Digital India” for
the last few years, and at the same time, making sure to use the Internet
shutdown as a tool of oppression. By using a proper communication shutdown and
blocking reporters, they made sure only the false stories from the state can
be reached to the readers/viewers of news across the world. But, a few brave
outside journalists and too many brave local journalists from Kashmir made
sure that they kept pushing the real news from the ground. They tried their
best to record atrocities.
This story in the New
Yorker
by Dexter Filkins should be the one for everyone to read. Take your time to
read how brave Rana Ayyub and the author managed to sneak into Kashmir, and
did the report.
Internet shutdowns across India
Now, if you think that the Indian government is doing this only in Kashmir,
then you are totally wrong. In the last few years, India saw the highest
number of Internet shutdowns across the country. Govt did not care about the
reason. Given any chance, they shut down the Internet. During the current
protests against the regime, they shut down the Internet in parts of
Delhi,
the capital of India. BBC did another story on why India gets the greatest number of Internet shutdowns.
To find all the instances of the shutdown, have a look at this site from SFLC India team.
Latest attack on students and professors of JNU
Jawaharlal Nehru University (JNU) is India’s topmost university, a place where
leaders of many different fields got their education, including Nobel
laureates. Yesterday evening a bunch of goons from the student wing (ABVP) of
the party in power (BJP), went inside of the campus (with the full support of
Delhi Police, who waited outside), and started attacking students and
professors with rods and other weapons. They turned off all the street lights,
but, as they forgot to shut down the Internet in the area, students managed to
send across SOS messages. Search #SOSJNU on Twitter to see the amount of
atrocity. Now, think for a second, what if they would have managed to shut
down the Internet before the attack, just like they are doing now in Kashmir
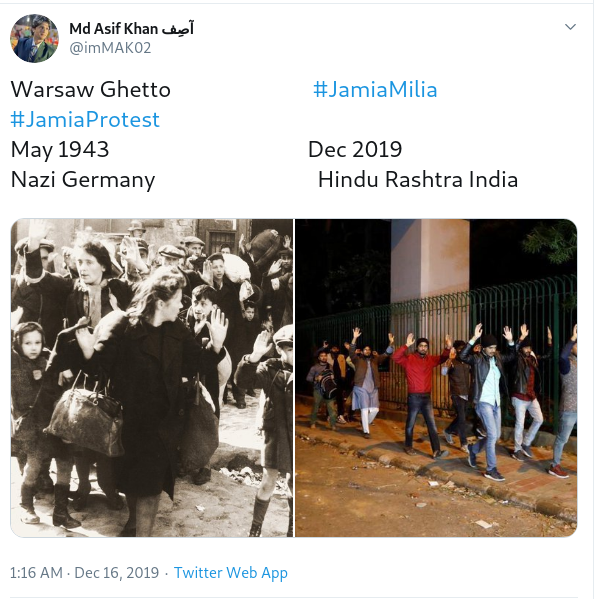
and many other parts of India. Economist and Nobel laureate Abhijit Banerjee
commented
how this “Echoes of Germany moving towards Nazi rule”.
Why should this matter to you, the technologist?
All of the technologies we are enjoying today, the modern world, the Internet
is one of the major bounding material of the same. Think about the pain and
oppression the people has to go through as this basic necessity is cut down
from their lives.
Most people do not have a voice to raise for themselves. If we don’t know,
then the whole country will be lost. And, we know from history what happens
next.
People still count India as a democracy, actually the largest in the world.
But, unless we raise up, the so-called democracy will be crushed the fascist
regime in no-time.
Quick point about different mesh-network and other solutions available at Internet shutdown time
We need more documentation and examples (also translated in local languages)
of the different tools available, which can help the citizens when the regime
is trying their best to shut down the Internet. India is also known for random
blocking of sites, and this is where free software like the Tor Project
becomes so essential.