Just like v2 Onion services, we can also set up client authorization for Onion
services v3. In simple terms, when you have a client authorization setup on an
Onion service, only the Tor clients with the private token can access the
service. Using this, you can run services (without opening up any port in your
system) and only selected people can access that service, that is also being
inside of totally encrypted Tor network. Last month, I did a workshop in
Rootconf about the same topic, but, I demoed v2
Onion services. In this blog post, I am going to show you how you can do the
same with the latest v3 services.
Setting up the Onion service
We assume that we are already running nginx or apache on port 80 of the
server. Add the following two lines at the end of the /etc/tor/torrc file of
your server.
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
Then, restart the tor service.
systemctl restart tor
The above command will create the onion service at
/var/lib/tor/hidden_service/ directory, and we can see the address from the
hostname file.
cat /var/lib/tor/hidden_service/hostname
cz2eqjwrned6s7zy3nrmkk3fjoudzhvu53ynq6gdny5efdj26zxf4bid.onion
It should also create a authorized_clients directory at the service
directory.
Next, we will create keys of type x25519, and you can either use any of the
following options to create the keys.
I used the Rust implementation, and I got the secret and the public key.
secret: "TIICFSKY2PECECM2LOA7XLKQKJWHYTN4WLRSIIJKQFCCL3K2II2Q"
public: "RO7N45JLVI5UXOLALOK4V22JLMMF5ZDC2W6DXVKIAU3C7FNIVROQ"
Now, we will use the public key to create a clientname.auth file in
/var/lib/tor/hidden_service/authorized_clients/ directory, I chose the name
kushal.auth.
descriptor:x25519:RO7N45JLVI5UXOLALOK4V22JLMMF5ZDC2W6DXVKIAU3C7FNIVROQ > /var/lib/tor/hidden_service/authorized_clients/kushal.auth
If you look closely, the file format is like below:
descriptor:x25519:public_key
Now, restart the tor service once again in the server.
systemctl restart tor
Setting up client authorization
The first step is to close down my Tor Browser as I will be manually editing
the torrc file of the same. Then, I added the following line to the same
file tor-browser_en-US/Browser/TorBrowser/Data/Tor/torrc.
ClientOnionAuthDir TorBrowser/Data/Tor/onion_auth
Next, we will create the directory.
mkdir tor-browser_en-US/Browser/TorBrowser/Data/Tor/onion_auth
chmod 0700 tor-browser_en-US/Browser/TorBrowser/Data/Tor/onion_auth
Then, add the following in kushal.auth_private file inside of the
onion_auth directory.
cz2eqjwrned6s7zy3nrmkk3fjoudzhvu53ynq6gdny5efdj26zxf4bid:descriptor:x25519:TIICFSKY2PECECM2LOA7XLKQKJWHYTN4WLRSIIJKQFCCL3K2II2Q
The format of the file:
onion_address_56_chars:descriptor:x25519:private_key
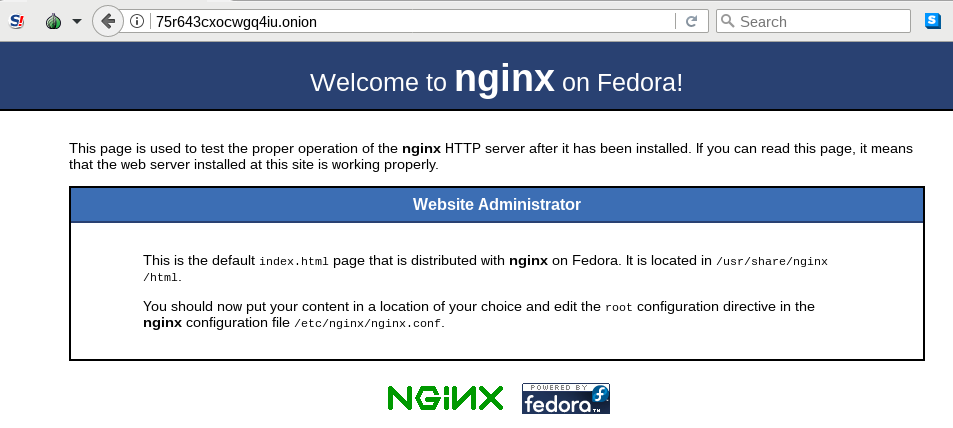
Now, start the Tor Browser, and you should be able to visit the authorized
Onion service at
cz2eqjwrned6s7zy3nrmkk3fjoudzhvu53ynq6gdny5efdj26zxf4bid.onion.
Use case for students
If you want to demo your web project to a selected group of people, but, don't
want to spend money to get a web server or VPS, Onion services is a great way
to showcase your work to the world. With the authenticated services, you can
choose whom all can view the site/service you are running.






 (Photo by Lalatendu)
(Photo by Lalatendu)
