I am happy to announce Tumpa 0.10.0 release.
Tumpa is a desktop application which allows you to
create OpenPGP keys and also allows uploading them to Yubikeys with a user
friendly GUI. With Tumpa, all you need is a few form inputs and few clicks, and
done! No more wrangling and breaking your head with command line interface.
This version is a complete rewrite of the initial
version I released
around 2 years ago. With the help from Elio and
his excellent team, we have a new design. Thank you
OTF for providing the funding for
the work.
Saptak & I decided that the code is ready to be
consumed. There are still things to work on, including the UI flows. In the
coming months we are going to add more features to the application to make it
super useful for advanced users too.
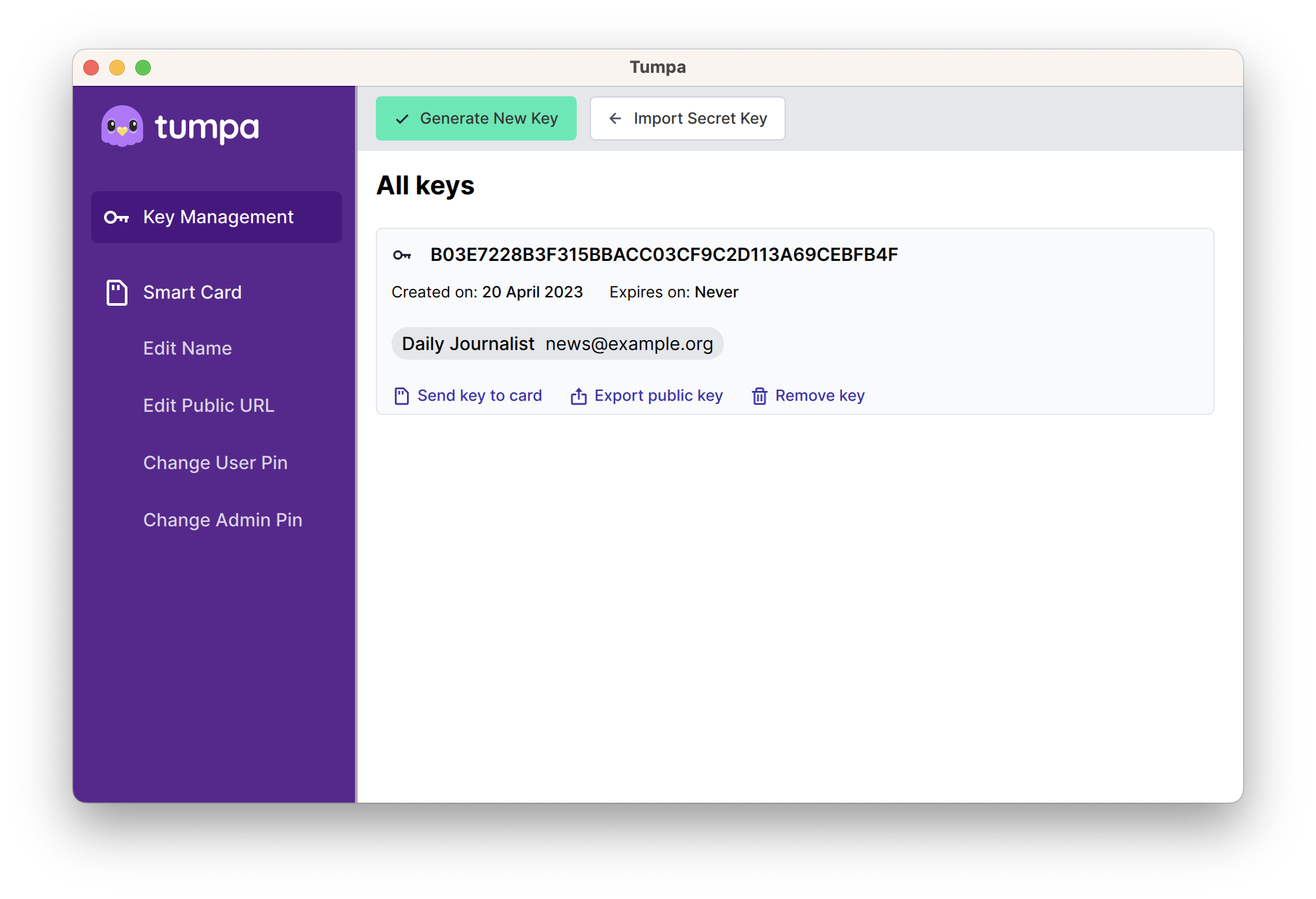
You can create Cv25519 or RSA4096 keys via the "Generate Key" button. You can
upload any key to an attached Yubikey, but remember that to use a Cv25519 key,
you will need Yubikey 5.
Installation
For Linux we have an AppImage and for Apple M1/M2 devices we have a dmg. You
can download them from the release
page. Remember to
have a look at the user
guide, specially
because you need to have pcscd service running on Linux.
Technologies used
This project works because we have
Johnnycanencrypt , a Python module written
in Rust to do OpenPGP operations (including Smartcard operations). Which in
turn uses Sequoia Project for the rust library to
create/manipulate OpenPGP keys.
The UI is made via QML, using PySide6. This
also shows that we can have decent looking desktop applications in Python.
The AppImage and Apple dmg files are available because of
briefcase project from
BeeWare team.
Give feedback
Since the focus of Tumpa is on making the use of OpenPGP with smart cards user
friendly and intuitive, we need a lot of feedback from the user. So, if you
find issues and have other feedback to improve the application, feel free to
submit [issues])(https://github.com/tumpaproject/tumpa/issues). We are also
available in #tumpa channel on IRC on libera.chat server. Feel free to ping the
IRC nicknames saptaks or kushal.