Hacker Ethic and Free Software Movement
We had a plan to go out on a short trip with the family on a Saturday. Our bags were packed, and everything was ready, but one tweet and its replies on Friday totally changed our plan.
We sent our daughter with my parents, for a day long holiday. We made amends for our absence with
- a pop-up wonder women doll,
- a promise to call her “Super Girl” the whole week, and
- to take her to the zoo the following weekend.
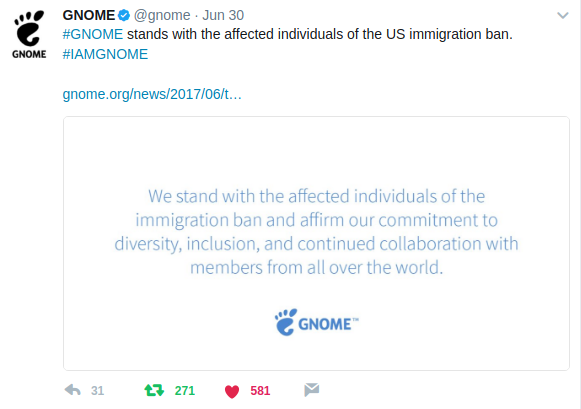
A few replies to the above tweet shook us from the inside out. Why? And how is it, that we who love to be called hackers do not know about the history of hacking? How are we so ignorant about the revolution, which we are a part of? Why don’t we not consider the politics, and the law as the base of this whole open source ecosystem? (May be this is why I, a lawyer, am being taunted as an outsider!)
Not knowing our history means we ignore the blood, sweat and tears of so many people who are fighting for our freedom. The freedom of users, our rights in the cyberspace are secure, only because of them.
Miguel de Icaza, the Gnome project founder replied in the same thread with the following tweet.
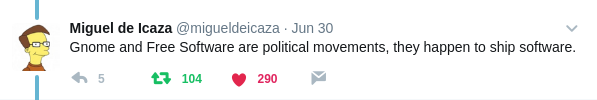
This made us keep discussing on the subject, the whole weekend. And we came up with the idea of telling people, the history of the present we live in, and enjoy.
Who are hackers?
I (Anwesha Das), was a mortgage attorney, and a Master of Law student back in 2012. I was attending the “FOSS.in” conference at Bangalore. The motto of conference, that year was, “Lets hack”.
That gave me a fright.
Oh, Lord? What have I done?
Did I go, get married to a criminal?
And have I now put myself in the middle of a bunch of criminals?
I, as a lawyer was thinking of the words, “hack” and “hacking” in the context of the Indian legal system. Specifically section 66 of the I.T Act, 2000. I had no choice, but to flee.
But then, I started observing the people around.
-
They were intelligent, smart and passionate workers. The only point of discussion was technology.
-
They felt, and behaved in a very respectable way when they called some one a hacker.
-
They really loved and enjoyed their work. (which is kind of rare in the profession I come from)
Was I understanding the term hacker correctly?
I got my answer at the conference itself; the real meaning of the word, hacker. Hack, (for these technical people) meant creating, inventing something. Hacking meant playful brilliance.
Hackers amaze people with their intelligence and innovation. They gave life to novel ideas which people thought were impossible to do; to wrought into reality. The hackers who I am surrounded with, create new things with the computer. But hacking does restrict itself to the boundaries of the computing realm. It can be done in any, and every sphere of life.
Why the word hacking go along with computers? The computer gives us a vast area to explore our creativity. It’s huge code base, and their intricacies and the complicated machines offer us opportunities to HACK.
I was soon befriending the hackers. I wasn’t afraid of them anymore nor holding the earlier (legal) connotation in my head.
The first thing I did after coming back from the conference — I created and put up a poster in my office door, (ignoring the frowning eyebrows of my lawyer friends).

The poster says, “Do not disturb, Hacking in progress.”
Hackers break the boundaries of possibility—not law. They invent laws, and policies to protect their innovations and ideas.
If we want to understand more, we need to look back in time. As Carl Sagan says,
“You have to know the past to understand the present.”
So, let’s roll out our Tardis and go to back to 1950s.
The Time 1955-1956 :
Place : Massachusetts Institute of Technology (MIT).
It was the age when mammoth computers ruled the world. It was the age of the TX-0. TX-0 (pronounced tixo) was an early, fully transistorized computer and contained a then-huge 64K of 18-bit words of magnetic core memory. It was located on the second floor of the famous, building 26, at the Research Laboratory of Electronics (RLE), at MIT,(which later spun off to become the MIT Artificial Intelligence Lab.) One had to use paper tapes to program for this beast. Before this computer, they had access to IBM computers (which were very restrictive in nature).
But the access to this machine was tightly controlled. Only few (lucky) people allowed were to work, to touch those precious machines. People who did not have official access to this computer started figuring out better ways to get access. Many people who booked time to access the computer may have skipped sleep at nights to gain time on the machine (think of access times like 3 AM), and an enthusiastic bunch (mostly from the Tech Model Railroad Club) would try to access the computer in those wee hours. Working on this computer became a lifestyle, may be one of the major reasons to live. These people; these original hackers — started staying back whole nights on the computer, and made sure no time was wasted.
The hackers: the revolutionaries
Working on the machine (TX0) created a new world, a new way of life. The culture that accompanied it, was built on different thoughts, a more utopian philosophy, dream and ethic.
The big machines came along with a great opportunity, hope, enormous of chance creation, innovation but unfortunately with little / rare access. They had so much to do but so little opportunity.
That laid down first rule of the Hacker Ethic.
Sharing, Decentralization, Openness, and free access stays at the core of the hacker ethic. These will lead to improvement of the society, the world at large, and the hackers’ world in particular.
Free Access:
Courtesy : Hackers: Heroes of the Computer Revolution by Steven Levy
Access to computers—and anything which might teach you something about the way the world works—should be unlimited and total.
Always yield to the Hands-On Imperative!
This boils down to the idea of a world, where you can fix things. If you think something is wrong, you should have the right to open it up, and fix it. A hacker does the same thing. She finds the problem and gets an answer to that. You can build new and exciting things on top of existing knowledge; like layers of nacre forming a pearl.
To work on or to make correct something wrong, one should have the full knowledge, and information of said thing. Thus, the first Hacker law set in stone was:
Free and Open Knowledge:
All information should be free.
There was to be no boundary around information.
The TX-0 came with almost no software. It offered hackers immense possibilities to hack. They engaged themselves working on the systems. They were building system tools which facilitated the working of other tools. They used to keep paper tapes (of the source code) in the drawer, so that the next person could read it and work on the next step.
This prevented the dread, time-wasting ritual of reinventing the wheel: instead of everybody writing his own version of the same program, the best version would be available to everyone, and everyone would be free to delve into the code and improve on that. A world studded with feature-full programs, bummed to the minimum, debugged to perfection.
Decentralization
Knowledge can be free and open only in a decentralized system. Thus, decentralization became one of the imperatives in the creating the perfect world of hackers. Where people / hackers are judged solely by their work and not by other factors.
Hackers should be judged by their hacking, not bogus criteria such as degrees, age, race, or position.
The Dream
Following these steps will help us reach our ultimate goal; a place where
- people / hackers share information
- knowledge is free and open
- everyone and anyone will have access to fix problems.
If you want to know more about the history of famous hacks at MIT, have a look at http://hacks.mit.edu/ .
The PDP-1 days
In 1961, a new computer from DEC was delivered to MIT, the PDP-1. The price for this computer was much lower compared to the TX-0. It was installed in the room right next to the TX-0. The hackers did not like the existing tooling (assembler) for PDP-1, and so over a weekend, a few people got together and converted the TX-0 assembler for use with the new computer. It was said, that were a similar effort made by the computer industry, it would have taken months of effort. Because of open information available, the hackers of MIT managed to showcase the value of the hacker ethic.
The source code of various programs was kept in drawers, for any one to access. People used to pick up work done by others, then improve the code, and put the new improved tapes right back in the drawer. This way everyone got the chance to learn from work of others and their improvements.
The Chess Story
After making a connection between the PDP-1 and the TX-0, the hackers invited Prof. John McCarthy to sit in front of it, and play a game of chess. The information was transferred to the TX-0 one bit at a time, where they had also invited another professor to sit. Both of them were told, they were playing against the computer. Only after playing the first few moves, McCarthy tried to find out the reason behind slow output, and then discovered the other professor in the TX-0 room.
Spacewar!
Steve Russell was one of the hackers who had used the TX-0 before and was then working on the PDP-1 system. He had the idea of making an application (a game) which would use the display system and some futuristic sci-fi story of two spaceships battling each other. But, to do so, he would require better sine-cosine routines (think about functions) for the display to work.
Kotok (who worked on the assembler), went to visit the DEC folks in a nearby city, and someone there provided him with the source code for the sine-cosine routines. After many intense six-eight hour sessions, in February 1962, they had the initial game ready. 2 ships firing torpedos at each other. But, as usual, the hackers at the lab thought of various improvements they could make, and the game got many new features over time. People would stand in line to play the game (whenever the system was free).
https://en.wikipedia.org/wiki/File:Spacewar!-PDP-1-20070512.jpg
Jumping into 1970
A freshman student from Harvard, Richard M. Stallman heard about the AI computer lab at MIT. He visited the place and found out how open the lab was (compared to Harvard’s computer labs). He also managed to get a job there to write a PDP-11 simulator to run on the lab’s PDP-10. From the very next week, he started visiting the place regularly and working on open terminals. He was introduced to hackers from the lab. He also liked the idea where hackers would do anything to keep access to the terminals open. That included picking the locks of the doors, removing ceiling tiles, or climbing walls. Even though there were many Academics in the AI Lab, the hacker ethic was accepted as a norm.
Stallman started visiting the lab routinely every weekend. A group of hackers used to go out together for dinner (mostly Chinese), and they used to come back and hack through the night. And sometimes at 3 AM they used to again go out for more Chinese food :) Many of the hackers used to stay up all night including Stallman.
During the 1970s, computer usage in the labs changed slowly. Many other users (of the other Operating Systems) slowly started adding security features to their systems, which included having password controlled access. The MIT computer science department did install such a system in 1977. Stallman managed to get access to the source code and wrote another program which would then decrypt the password. He mailed the users with a message to change their password to a “carriage return” (just pressing the enter key). All most one-fifth of the staff agreed to this, and they had empty passwords.
Stallman joined MIT as a Physics grad student. He spent months in the Lab (he had no apartment at the time). By October 1975, he left his grad classes, and started working in the AI Lab full time. The lab was filled with plenty of such individuals, who never finished their academic degrees.
The homegrown operating system for the Lab's PDP-10 was called the Incompatible Time Sharing system (ITS). The name was pun on the lab’s original operating system, the Compatible Time Sharing System (CTSS). ITS was written and maintained by the folks in the Lab.
TECO and the Birth of Emacs
Text Editor and COrrector was the primary editor in the AI Lab. One had to give long edit commands ending with a “end of command string” sequence. That meant one could not see the text while editing it. It was upgraded from the PDP-6 days, and with a special hack it used to show both the original text, and a place to enter command strings in a split screen.
Richard Stallman found a hack called “Ctrl-R” for TECO, where by pressing those two keys, one could use the editor on a keystroke to keystroke basis. But, it used to take only the first 5 rows on the top of the screen. Stallman hacked it to use the whole screen, and (more importantly) anyone could now save their macros to some set of fixed keystrokes. This created a new revolution; that of using macros. Everyone started creating their own macro packages, and their own keystrokes. This also brought the issue of too much customization, since one hacker could not sit in front of another hacker's terminal and use it. Guy Steele, another hacker in the lab decided to do something to solve this issue. He started creating a chart of macro commands along with 4 different macro packages. This project got the attention of Stallman, and he started looking into it with more attention. Finally, this gave birth to a new project, named Emacs, for editing macros. People slowly started adopting this new editor. But, there was a good chance that people would write or develop some special features, which others would want to use. And so, in the Emacs documentation, Stallman added a contract (he looked at it as a social contract) saying Emacs “was distributed on a basis of communal sharing, which means that all improvements must be given back to me to be incorporated and distributed.” This allowed Stallman to add useful features (from the users) to Emacs, and share the improved work anew.
The Story of Pretty Printing
Steele also had the idea to add a feature that would reformat source code, so that it would more readable. One morning he sat down at the terminal, with Stallman looking over his shoulder, and they both worked on this feature for the next 10 hours. At the end they made it; within a 100 lines. Later while describing how focused the session was, Steele said the following.
My first thought afterward was [that] it was a great experience, very intense, and that I never wanted to do it again in my life.
The Unix story
The Unix operating system grew in popularity during 1970s. Here is a famous picture of Ken Thompson and Dennis Ritchie working on a PDP-11 computer (this is most probably taken during the time they wrote Unix in C programming language). People had to purchase licenses from AT&T to use Unix. Around 1975, Berkeley university also started working on their own Unix operating system, known as BSD. But, to get a copy of the BSD tape, one had to produce a copy of AT&T license, as BSD had code from AT&T Unix.
Lisp machines
Now if we look back what else was happening in the AI during those days, one major project was Lisp machines. Richard Greenblatt and Thomas Knight started building computers which could run lisp instructions at the hardware level, known as MIT Lisp Machines. This is an early version of one such lisp machine.
Symbolics and LMI
By 1980, two companies sprung from the Lisp machine work in the AI Lab. Symbolics had external funding, and also managed to get 14 hackers from the lab to work on their version of the Lisp machine. On the other side was LISP Machines, Inc. (LMI), which had Greenblatt leading the team, comprising of the rest of the hackers from the AI Lab (except RMS). Both the groups worked at the AI Lab, and had licensed the Lisp Machine operating system code from MIT. According to the license, they had to return any improvement of the code back to the MIT (so that MIT could use the code). Even though license did not mention anything about the redistribution of those changes, they allowed it as an gentleman’s agreement, as everyone benefited from the work.
But, on March 16, 1982, Symbolics decided to stop sharing code, electing to enforce the letter of the license. The AI LAB had to choose to honor the Symbolics license and switch to a Symbolics machine if they were to get newer updates. The hope was to destroy LMI as a competitor. This made RMS vengefully, choose a side (LMI). He started reading the changes made by Symbolics, and re-implementing them (in a completely different way) into MIT Lisp Machine Operating system. The executives from Symbolics installed a spy program on Stallman’s terminal to find evidence against him. When (in early 1983) these were presented to the AI Lab administrators, Stallman successfully showcased how his work was different, and any similarity in the code was from before the fork of the source code. The Lab administrators allowed him to continue his work. Stallman also started reading only the documentation from Symbolics (without reading the source code), and implementing the features into the MIT Lisp Machine. LMI thus had access to the changes made by RMS, benefitting from the work, just like all other users of the MIT Lisp Machines in the Lab.
In RMS’s own words…
I was going to punish Symbolics if it was the last thing I did.
This also brought changes within personal relationships. The same hackers who used to go out for dinner together, started going out in different groups. The estrangement went up to such levels where some old friends even started avoiding RMS (or lying to him) about such trips.
Stallman stood his ground and kept adding similar features to the MIT Lisp Machine (also providing the same to LMI.) Symbolics had a group of legendary hackers working on their system, but on the other side RMS worked alone on these features. This made him special, even to the people from the Symbolics group. Levy’s book has a comment from Bill Gosper.
I can see something Stallman wrote, and I might decide it was bad (probably not, but somebody could convince me it was bad), and I would still say, “But wait a minute – Stallman doesn’t have anybody to argue with all night over there. He’s working alone! It’s incredible anyone could do this alone!”
Changing the World
But, while RMS was fighting this war, the world of computers was also changing very fast. There were many personal computers released and their software came without any source code, and under NDAs (Non disclosure agreements), and EULAs (End User License Agreements).
Story of a Printer
In 1980, the then 27 year old RMS was waiting for a 50 page print job to be done. This was supposed to be printed on a printer made & gifted by Xerox Palo Alto Research Facility. But, it was stuck, and not for the first time. Like many other problems, Stallman wanted to fix this issue, but he could not find any corresponding source code for the system. Later he figured out that some researcher in the Carnegie Mellon university had access to the source code. A few months later, when he visited the university, he met the researcher and asked for a copy of the source, which the researcher refused. One reason was a nondisclosure agreement (NDA) he signed with Xerox. This was RMS's first encounter with an NDA. To him this was the path to betray all users, making them victims of proprietary software.
GNU & the FSF
On September 27, 1983, Stallman sent out an announcement over Usenet newsgroup net.unix-wizards about a new New UNIX implementation.
Starting this Thanksgiving I am going to write a complete Unix-compatible software system called GNU (for Gnu’s Not Unix), and give it away free to everyone who can use it. Contributions of time, money, programs and equipment are greatly needed.
He also added a note about himself.
I am Richard Stallman, inventor of the original much-imitated EMACS editor, now at the Artificial Intelligence Lab at MIT. I have worked extensively on compilers, editors, debuggers, command interpreters, the Incompatible Timesharing System and the Lisp Machine operating system. I pioneered terminal-independent display support in ITS. In addition I have implemented one crashproof file system and two window systems for Lisp machines.
In January, 1984, Stallman resigned from the MIT staff, so that he could work on GNU without any legal hurdles. In 1985 he released GNU Emacs, and followed it up with The GNU Manifesto (soon after the original announcement). As the popularity of GNU Emacs in the Unix community slowly started rising, Stallman founded the Free Software Foundation (FSF) with help from friends. He became the president, and other friends joined the board of directors. Robert Chassell (who worked at LMI) was one of the board members, and helped as Treasurer of the foundation. He also wrote really great documentation, and later wrote the manual for Emacs Lisp. The FSF also started sending out bulletins, you can read the first bulletin; and became the face of GNU. Free as in Freedom became the center of focus.
In 1985, along with a release of Emacs, RMS also introduced a General Public License for Emacs. Which he later hacked more on, and gave birth to The GNU General Public License (GPL). The 1.0 version of the license was released in 1989.
By January 1987, GNU ls, grep, make, ld were already out in the world. Someone wrote the first copy of the free tar utility. cron, at and m4 commands were also getting ready. awk was in its final testing stage, and people were still writing the diff command. gdb was already written in 1986 (running only on Vax, Suns). GNU cc was also getting ready (it could generate good Vax code, and also good 68000 and 68020 code). They expected to release the complete system by 1987 itself. GNU Chess, Bison, and the X Window System were also ready MIT Scheme was ready to be used (but without any documentation).
LMI provided office space, computer resources, and a mailing address for the foundation.
By February 1988, Berkeley Unix started releasing parts of their Unix as Free Software. They also started using GNU make, awk, sh from the GNU project. They also had planned to release csh (from BSD) as free software. Brian Fox started implementing the Bourne-again Shell (Bash), and it was completed by June of the same year. GNU Make was also marked as ready for release. Ronald McGrath also almost finished a complete set of the ANSI C library. GNU malloc, regexp, and the termcap library were already ready. Ghostscript was also supposed to be finished by March (by Peter Deutsch). Furthermore, Michael Tiemann wrote the GNU C++ compiler as an extension of GCC, along with GDB+, to debug C++ code. Tiemann was a graduate student at Stanford University, keeping a close watch on GNU development. In 1990, along with John Gilmore and David Henkel-Wallace, Tiemann started a new software consulting company called Cygnus (Cygnus, Your GNU Support). By the end of first year, they had contracts worth $725,000. They were marked as the first for-profit corporation providing commercial support exclusively for free software.
NeXT, Inc. also started using GNU Emacs, GCC, GAS and GDB in their operating system, thus becoming the first computer manufacturer to do so.
By mid 1990, FSF was shipping Emacs Lisp reference manual, it was 550 pages, and cost $50.
The Story of the Kernel
In 1991, a Finnish student, Linus Torvalds, wrote a mail about his hobby project, a kernel for an operating system (for 386 clones). He had already ported Bash to it. For the 0.1 (the first one) release, it used its own license. In December 1992, he released the 0.99 version of Linux kernel using the GNU GPL license.
The kernel, along with many other GNU projects created a perfect storm; a complete operating system to be used by the Free Software followers. The void of a working kernel in the GNU project was filled up by the Linux kernel. This is why RMS calls the operating system GNU/Linux rather than the term many people use, Linux.
By 1993, there were over 100 developers working on this new kernel. Slackware, the first distribution (still in use) came out. The Debian project also started later that same year.
In 1994, Mark Ewing started the Red Hat Linux distribution. It soon merged with Bob Young’s ACC Corporation, and the new company was named Red Hat Software. In August 11, 1999, Red Hat went public, and later in November it acquired Cygnus. Michael Tiemann became the CTO of the company. Currently he is serving as vice president of open source affairs.
Open Source
Meanwhile in Palo Alto, California, in 1998, a group of free software folks met, and Christine Peterson suggested the term “Open Source” as it was a better fit (in their eyes) for companies who were scared to install and use free software. Later, in February, 1998, Bruce Perens and Eric S. Raymond founded Open Source Initiative (OSI).
And the momentum continued ...
If you are reading this post, you’ve most probably heard the term "Open Source" many times before. Now, you’ve also read about the history of Free Software movement. This is even more important now, in our time, in our daily lives. Between so many different SAAS (Software as a service) Cloud providers, DRM (Digital rights management) tools, and Net Neutrality issues, the fight for users' freedom is even more important. Be the part of revolution, spread freedom as far and as wide as you can.
Books to read on the subject:
Written by: Anwesha Das, Kushal Das, editited by: Jason Braganza