How to configure Tor onion service on Fedora

You can set up a Tor onion service in a VM on your home desktop, or on a Raspberry Pi attached to your home network. You can serve any website, or ssh service using the same. For example, in India most of the time if an engineering student has to demo a web application, she has to demo on her laptop or on a college lab machine. If you set up your web application project as an onion service, you can actually make it available to all of your friends. You don’t need an external IP or special kind of Internet connection or pay for a domain name. Of course, it may be slower than all the fancy website you have, but you don’t have to spend any extra money for this.
In this post, I am going to talk about how can you set up your own service using a Fedora 26 VM. The similar steps can be taken in Raspberry Pi or any other Linux distribution.
Install the required packages
I will be using Nginx as my web server. The first step is to get the required
packages installed.
$ sudo dnf install nginx tor
Fedora 26 - x86_64 - Updates 10 MB/s | 20 MB 00:01
google-chrome 17 kB/s | 3.7 kB 00:00
Qubes OS Repository for VM (updates) 98 kB/s | 48 kB 00:00
Last metadata expiration check: 0:00:00 ago on Wed Jan 17 08:30:23 2018.
Dependencies resolved.
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
nginx x86_64 1:1.12.1-1.fc26 updates 535 k
tor x86_64 0.3.1.9-1.fc26 updates 2.6 M
Installing dependencies:
gperftools-libs x86_64 2.6.1-5.fc26 updates 281 k
nginx-filesystem noarch 1:1.12.1-1.fc26 updates 20 k
nginx-mimetypes noarch 2.1.48-1.fc26 fedora 26 k
torsocks x86_64 2.1.0-4.fc26 fedora 64 k
Transaction Summary
================================================================================
Install 6 Packages
Total download size: 3.6 M
Installed size: 15 M
Is this ok [y/N]:
Configuring Nginx
After installing the packages, the next step is to setup the web server. For a
quick example, we will just show the default Nginx index page over this web
service. Please read about Nginx to know more about how to configure Nginx
with your web application.
Here we have the web server running on port 80 by default.
Configuring Tor
Next, we will set up the Tor onion service. The configuration file is located
at /etc/tor/torrc. We will add the following two lines.
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
We are redirecting port 80 in the onion service to the port 80 in the same system.
Starting the services
Remember to open up port 80 in the firewall before starting the services. I am going to keep it an exercise for the reader to find out how :)
We will start nginx and tor service as the next step, you can also watch
the system logs to find out status of Tor.
$ sudo systemctl start nginx
$ sudo systemctl start tor
$ sudo journalctl -f -u tor
-- Logs begin at Thu 2017-12-07 07:13:58 IST. --
Jan 17 08:33:43 tortest Tor[2734]: Bootstrapped 0%: Starting
Jan 17 08:33:43 tortest Tor[2734]: Signaled readiness to systemd
Jan 17 08:33:43 tortest systemd[1]: Started Anonymizing overlay network for TCP.
Jan 17 08:33:43 tortest Tor[2734]: Starting with guard context "default"
Jan 17 08:33:43 tortest Tor[2734]: Opening Control listener on /run/tor/control
Jan 17 08:33:43 tortest Tor[2734]: Bootstrapped 5%: Connecting to directory server
Jan 17 08:33:44 tortest Tor[2734]: Bootstrapped 10%: Finishing handshake with directory server
Jan 17 08:33:44 tortest Tor[2734]: Bootstrapped 15%: Establishing an encrypted directory connection
Jan 17 08:33:45 tortest Tor[2734]: Bootstrapped 20%: Asking for networkstatus consensus
Jan 17 08:33:45 tortest Tor[2734]: Bootstrapped 25%: Loading networkstatus consensus
Jan 17 08:33:55 tortest Tor[2734]: I learned some more directory information, but not enough to build a circuit: We have no usable consensus.
Jan 17 08:33:55 tortest Tor[2734]: Bootstrapped 40%: Loading authority key certs
Jan 17 08:33:55 tortest Tor[2734]: Bootstrapped 45%: Asking for relay descriptors
Jan 17 08:33:55 tortest Tor[2734]: I learned some more directory information, but not enough to build a circuit: We need more microdescriptors: we have 0/6009, and can only build 0% of likely paths. (We have 0% of guards bw, 0% of midpoint bw, and 0% of exit bw = 0% of path bw.)
Jan 17 08:33:56 tortest Tor[2734]: Bootstrapped 50%: Loading relay descriptors
Jan 17 08:33:57 tortest Tor[2734]: Bootstrapped 56%: Loading relay descriptors
Jan 17 08:33:59 tortest Tor[2734]: Bootstrapped 65%: Loading relay descriptors
Jan 17 08:34:06 tortest Tor[2734]: Bootstrapped 72%: Loading relay descriptors
Jan 17 08:34:06 tortest Tor[2734]: Bootstrapped 80%: Connecting to the Tor network
Jan 17 08:34:07 tortest Tor[2734]: Bootstrapped 85%: Finishing handshake with first hop
Jan 17 08:34:07 tortest Tor[2734]: Bootstrapped 90%: Establishing a Tor circuit
Jan 17 08:34:08 tortest Tor[2734]: Tor has successfully opened a circuit. Looks like client functionality is working.
Jan 17 08:34:08 tortest Tor[2734]: Bootstrapped 100%: Done
There will be a private key and the hostname file for the onion service in the
/var/lib/tor/hidden_service/ directory. Open up Tor
browser, and visit the
onion address. You should be able to see a page like below screenshot.
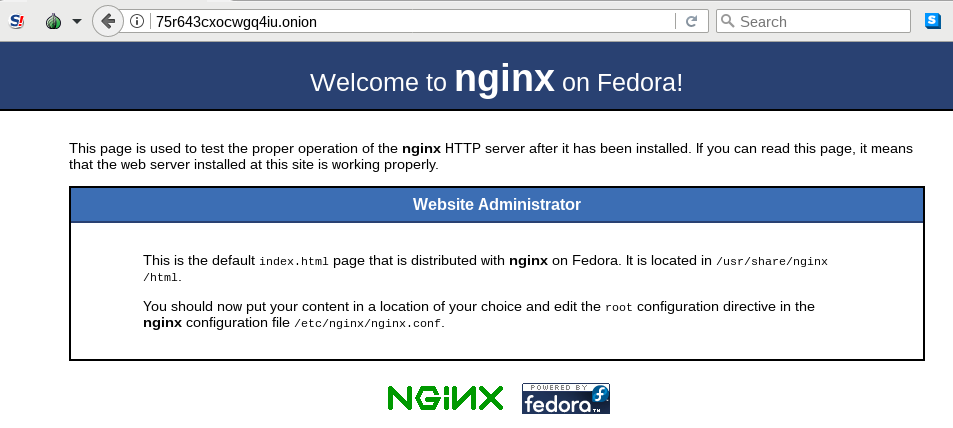
Remember to backup the private key file if you want to keep using the same onion address for a longer time.
What all things can we do with this onion service?
That actually depends on your imagination. Feel free to research about what all different services can be provided over Tor. You can start with writing a small Python Flask web application, and create an onion service for the same. Share the address with your friends.
Ask your friends to use Tor browser for daily web browsing. The more Tor traffic we can generate, the more difficult it will become for the nation-state actors to try to monitor traffics, that in turn will help the whole community.
WARNING on security and anonymous service
Remember that this tutorial is only for quick demo purpose. This will not make your web server details or IP or operating system details hidden. You will have to make sure of following proper operational security practices along with system administration skills. Riseup has a page describing best practices. But, please make sure that you do enough study and research before you start providing long-term services over the Tor.
Also please remember that Tor is developed and run by people all over the world and the project needs donation. Every little bit of help counts.