Introduction to Qubes
I heard the name Qubes OS as an Operating System which was built while keeping security in mind, and also they used Fedora as the base Operating System. A reasonably secure operating system is the tagline and they also have a few testimonials in the site, I guess the most famous one is the following tweet.

The name again came up this week. This time I thought of trying it out, but, this is something I had to do on a bare-metal box, than on a VM. Luckily I bought extra drives in the last PyCon trip. I downloaded the stable 3.2 release, but the installer was failing into a Dracut shell saying /dev/mapper/live-rw is write protected. So, I moved on to the 4.0RC1 image. The installer is a modified Anaconda, means something very familiar to any Fedora/CentOS/Red Hat user. 4.0RC1 is based on Fedora 25, means more known points there.
Qubes uses Xen to manage VMs (for the rest of the post, I will keep using both VM, and domain interchangeably). The dom0 is the initial domain which comes up on boot. It is a short form of Domain 0. This is a privileged domain which manages all the other domains (domU). The default desktop for 4.0rc1 is XFCE. The dom0 does not have standard networking enabled. Actually, to have a working network to connect to outside world, the OS creates two special VMs.
sys-firewall
This special VM is the firewall for every other application VMs. You can actually create more than one firewall VMs and have a different set of rules.
sys-net
This VM has access to the network hardware and can create a connection with your local Wi-Fi or LAN/cable network. In my case, Fedora was failing to create internal interfaces which are being used by sys-firewall, so I rebooted the VM with a Debian-8 template. It solved my networking issue.
Regular Application VMs
When you first install the system, the installer will create a few domains for you, personal, work, untrusted, vault. It will create proper application shortcuts in the menu. This means when you click on the application menu for the Terminal for personal domain, it will first start the domain, and then open up the gnome-terminal for you. Each domain also gets a /rw partition which gets mounted as home. For every reboot, they start from a clean template, with only home consistent between boots.
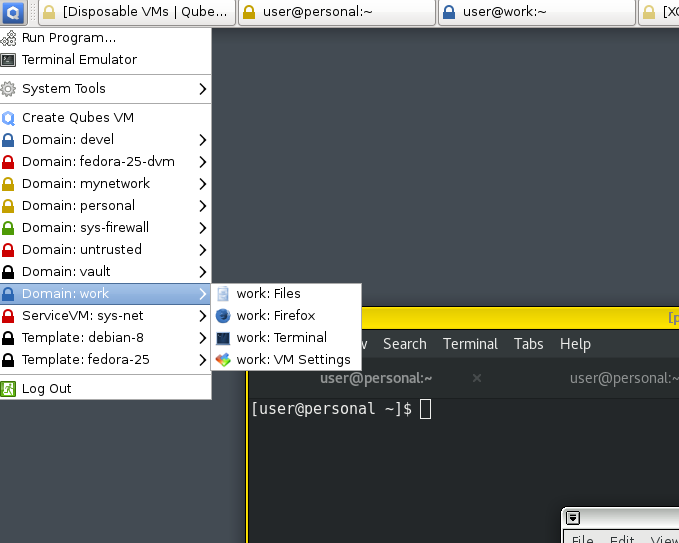
This also means there is no easy way for applications/malware to talk between different VMs. If you open up a wrong website (with malware) on the untrusted domain, it will not have access to the filesystem under your work domain. There are special ways to copy/paste text between domains.
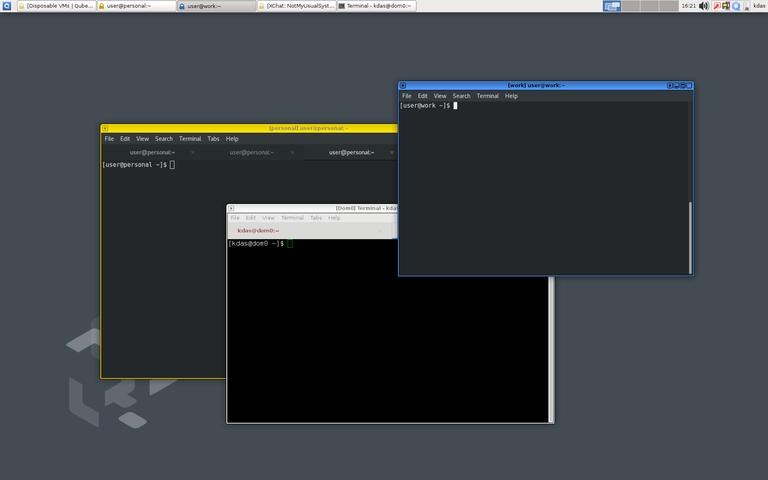
You can see in the above screenshot, the applications from each domain have different colors, that helps for quick recognition of each application for different domains. You can also see details about the running VMs by clicking on the Qubes icon on the tray in the menubar.

Disposable domains
There are times when you want to open a downloaded file (say PDF or a spreadsheet) on a VM which is only for single use. As soon as you close the application, the VM gets destroyed. For more details, read this document.
VMs without network access
The Vault is a special domain which does not connect to any network. You can also create new VMs in the same way, which does not connect to any firewall VM. The isolation from the network means nothing will go out in case of a malware in the file.
The following screenshot is showing the output of the qvm-ls command in dom0.

I will write more posts in future as I figure out things. Running F26 on the VMs is one them, because Python3.6 :) #qubes channel on Freenode is not that very active, but you will be able to find help in the channel if you wait.