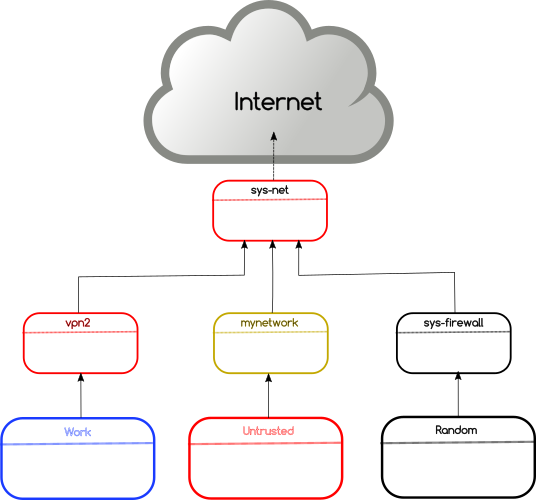
Network isolation using NetVMs and VPN in Qubes
In this post, I am going to talk about the isolation of network for different domains using VPN on Qubes. The following shows the default network configuration in Qubes.
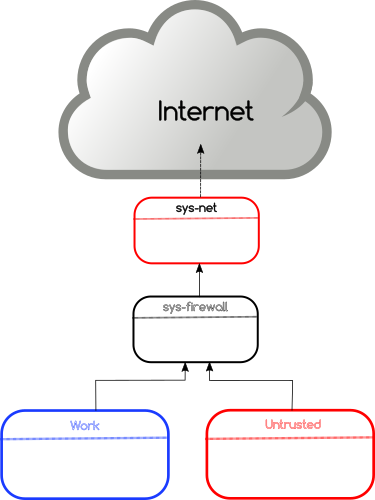
The network hardware is attached to a special domain called sys-net. This is the only domain which directly talks to the outside network. Then a domain named sys-firewall connects to sys-net and all other VMs use sys-firewall to access the outside network. These kinds of special domains are also known as NetVM as they can provide network access to other VMs.
Creating new NetVMs for VPN
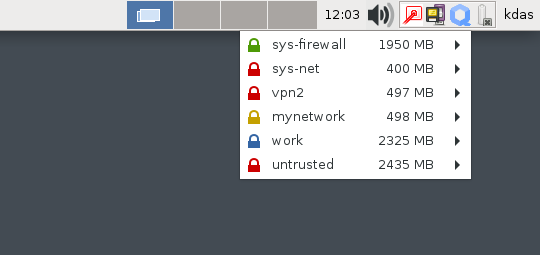
The easiest way is to clone the existing sys-net domain to a new domain. In my case, I have created two different domains, mynetwork and vpn2 as new NetVMs in dom0.
$ qvm-clone sys-net mynetwork
$ qvm-clone sys-net vpn2
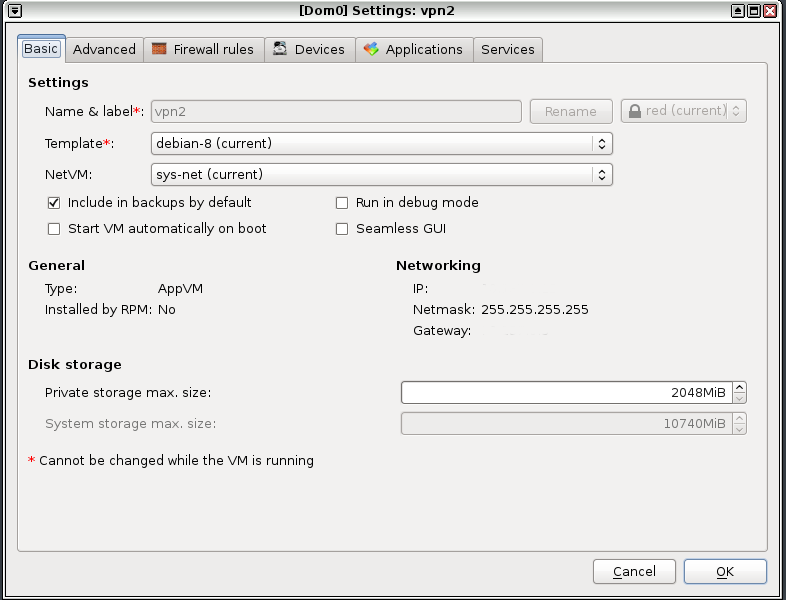
As the next step, I have opened the settings for these VMs and marked sys-net as the NetVM for these. I have also install openvpn package in the templateVM so that both the new NetVM can find that package.
Setting up openvpn
I am not running openvpn as proper service as I want to switch to different VPN services I have access to. That also means a bit of manual work to setup the right /etc/resolv.conf file in the NetVMs and any corresponding VMs which access the network through these.
$ sudo /usr/sbin/openvpn --config connection_service_name.ovpn
So, the final network right now looks like the following diagram. The domains (where I am doing actual work) are connected into different VPN services.