Introducing Tumpa, to make OpenPGP simple with smartcards
Generating OpenPGP keys in an offline air-gapped system and then moving them
into a smart card is always a difficult task for me. To remember the steps and
command-line options of gpg2 correctly and then following them in the same
order is difficult, and I had trouble enough number of times in doing so when I
think about someone who is not into the command line that much, how difficult
these steps are for them.
While having a chat with Saptak a few weeks ago, we came up with the idea of writing a small desktop tool to help. I started adding more features into my Johnnycanencrypt for the same. The OpenPGP operations are possible due to the amazing Sequoia project.
Introducing Tumpa
The work on the main application started during the holiday break, and today I
am happy to release 0.1.0 version of
Tumpa to make specific OpenPGP operations
simple to use. It uses Johnnycanencrypt inside, and does not depend on the gpg.
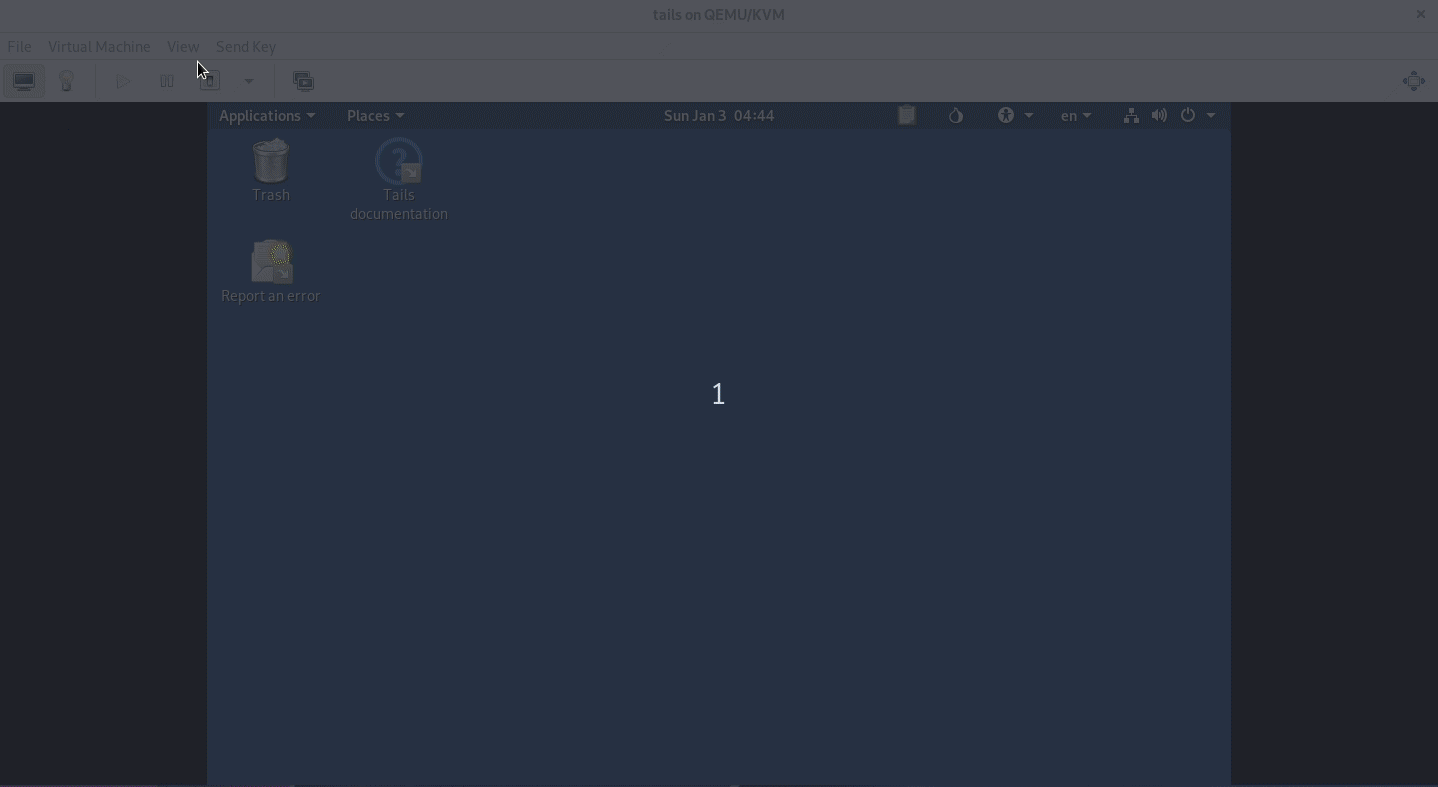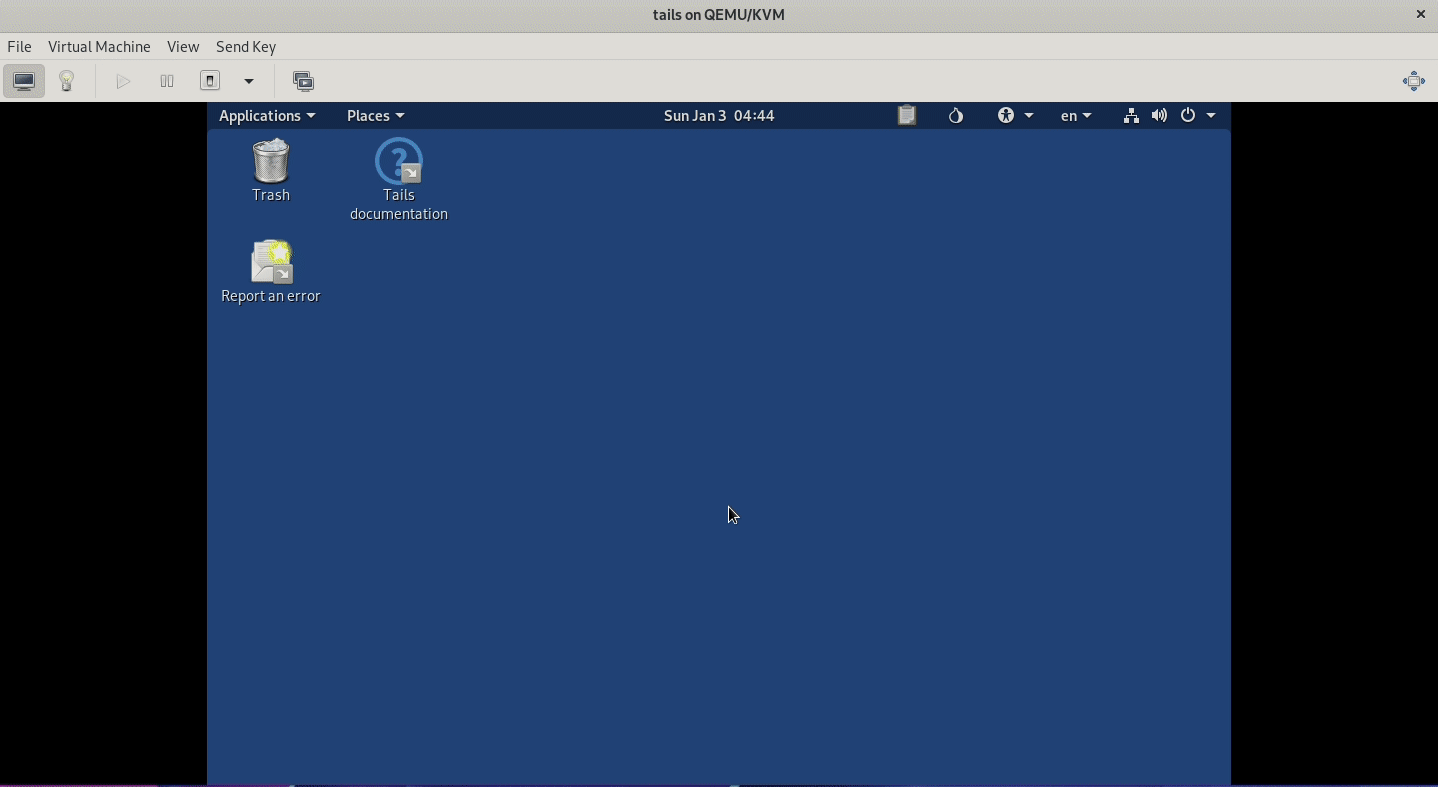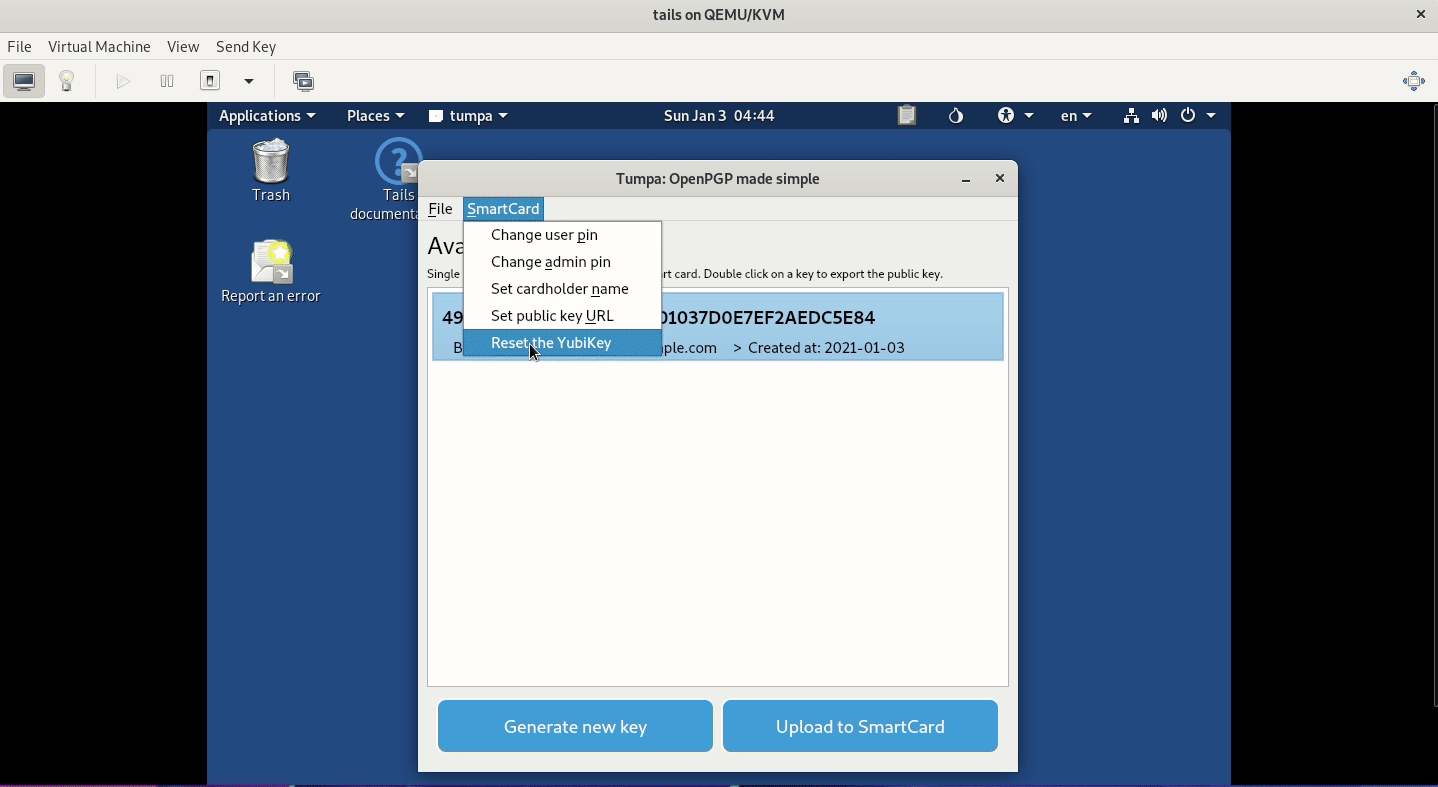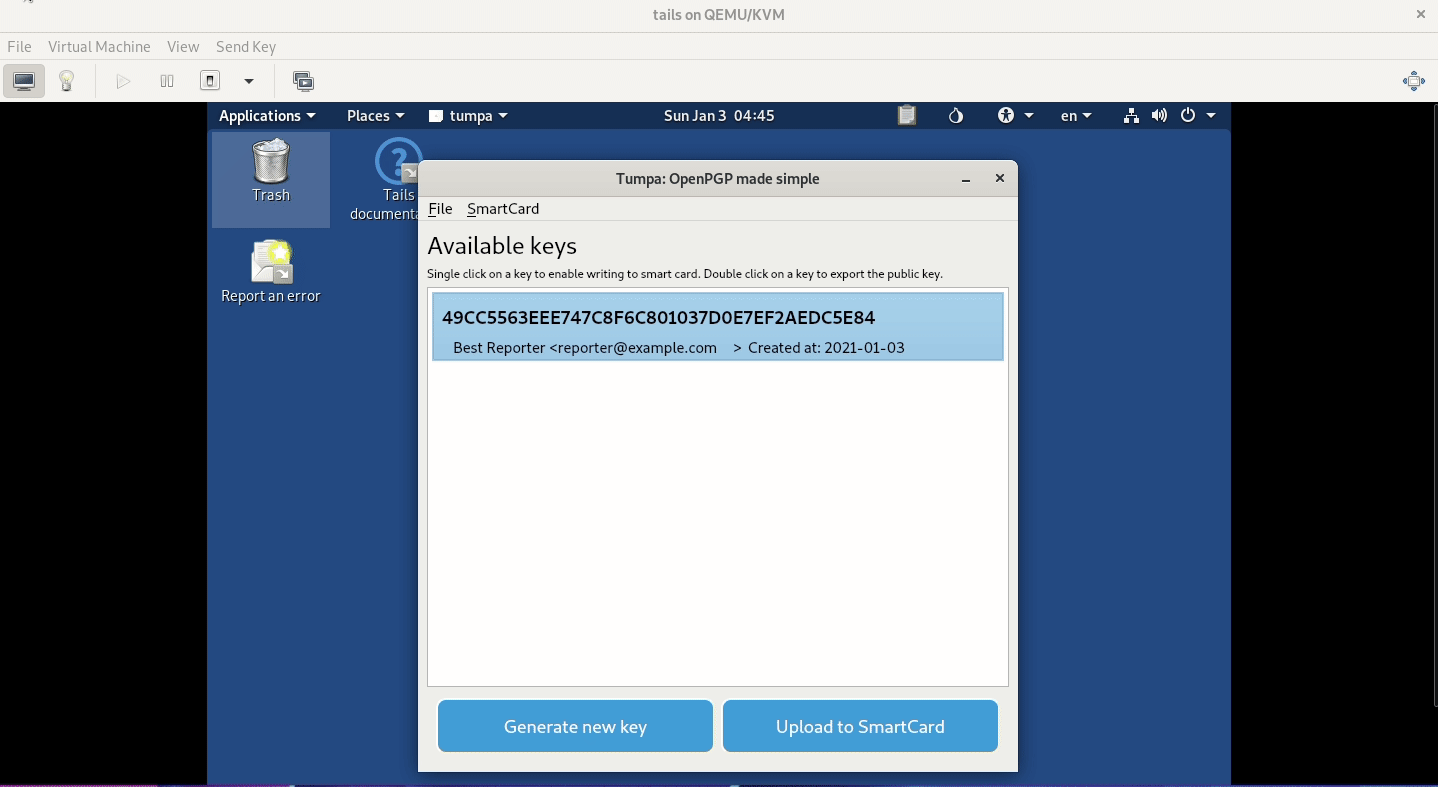
Here is a small demo of the application running in a Tails (VM) environment. I am creating a new OpenPGP key with encryption and signing subkeys, and then putting them into a Yubikey. We are also setting the card holder's name via our tool.
We can also reset any Yubikey with just a click.
You can download the Debian Buster package for Tails from the release page from Github. You can run from the source in Mac or Fedora too. But, if you are doing any real key generation, then you should try to do it in an air-gapped system.
You can install the package as dpkg -i ./tumpa_0.1.0+buster+nmu1_all.deb inside of Tails.
What are the current available features?
- We can create a new OpenPGP key along with selected subkeys using Curve25519. By default, the tool will add three years for the expiration of the subkeys.
- We can move the subkeys to a smart card. We tested only against Yubikeys as that is what we have.
- We can set the name and public key URL on the card.
- We can set the user pin and the admin pin of the smart card
- We can reset a Yubikey.
- We can export the public key for a selected key.
What is next?
A lot of work :) This is just the beginning. There are a ton of features we planned, and we will slowly add those. The UI also requires a lot of work and touch from a real UX person.
The default application will be very simple to use, and we will also have many advanced features, say changing subkey expiration dates, creating new subkeys, etc. for the advanced users.
We are also conducting user interviews (which takes around 20 minutes of time). If you have some time to spare to talk to us and provide feedback, please feel free to ping us via Twitter/mastodon/IRC.
We are available on #tumpa channel on Freenode. Come over and say hi :)
There are a lot of people I should thank for this release. Here is a quick list at random. Maybe I miss many names here, but you know that we could not do this without your help and guidance.
- Sequoia team for all the guidance on OpenPGP.
- Milosch Meriac for providing the guidance (and a ton of hardware).
- Vincent Breitmoser, for keep explaining OpenKeyChain codebase to me to understand smart card operations
- Anwesha Das for fixing the CI failures for Johnnycanencrypt, and documentation PRs.
- Harlo and Micah, for all the amazing input for months.
- Saptak Sengupta for being the amazing co-maintainer.