I dream of a day, and it is not a crazy dream, when everybody on this planet
who wants to know all about that is presently known about something, will be
able to do so regardless of where he or she is. And and I dream of a day where
the right to know is understood as a natural human right, that extends to every
being on the planet who is governed by anything. The right to know what it’s
government is doing and how and why. -- John Perry Barlow

I met John Perry Barlow only
once in my life, during his PyCon US 2014 keynote. I remember trying my best
to stay calm as I walked towards him to start a conversation. After some time,
he went up on the stage and started speaking. Even though I spoke with him
very briefly, I still felt like I knew him for a long time.
This Saturday, April 7th, Electronic Frontier Foundation and
Freedom of the Press Foundation organized the John
Perry Barlow
Symposium at the
Internet Archive to celebrate the life and leadership of
John Perry Barlow, or JPB as he was known to many of his friends and followers.
The event started around 2:30AM IST, and Anwesha and /me woke up at right time
to attend the whole event. Farhaan and Saptak also took part in watching the
event live.
Cory Doctorow was set to open the event but was late due to closing down of SFO
runways (he later mentioned that he was stuck for more than 5 hours). In his
stead, Cindy Cohn, Executive Director of the Electronic Frontier Foundation,
started the event. There were two main panel sessions, with 4 speakers in each,
and everyone spoke about how Barlow inspired them, or about Internet freedom,
and took questions after. But, before those sessions began, Ana Barlow spoke
about her dad, and about how many people from different geographies were
connected to JPB, and how he touched so many people’s lives.

The first panel had Mitch Kapor, Pam Samuelson, Trevor Timm on the stage. Mitch
started talking with JPB’s writing from 1990s and how he saw the future of
Internet. He also reminded us that most of the stories JPB told us, were
literally true :D. He reminded us even though EFF started as a civil liberties
organization, but how Wall Street Journal characterized EFF as a hacker
defense fund. Pam Samuelson spoke next starting with a quote from JPB. Pam
mentioned The Economy of Ideas
published in 1994 in the Wired magazine as the Barlow’s best contribution to
copyrights.

Cory Doctorow came up on stage to introduce the next speaker, Trevor Timm, the
executive director of Freedom of the Press Foundation (FPF). He particularly
mentioned SecureDrop project and the importance of
it. I want to emphasize one quote from him.
It’s been observed that many people around the world, billions of people
struggle under bad code written by callow silicon valley dude bros, those who
hack up a few lines of code and then subject billions of people to it’s
outcomes without any consideration of ethics.


Trevor talked about the initial days of Freedom of the Press Foundation, and
how JPB was the organizational powerhouse behind the organization. On the day
FPF was launched, JPB and Daniel Ellsberg wrote an
article
for Huffingtonpost, named Crowd Funding the Right to Know.
When a government becomes invisible, it becomes unaccountable. To expose its
lies, errors, and illegal acts is not treason, it is a moral responsibility.
Leaks become the lifeblood of the Republic.
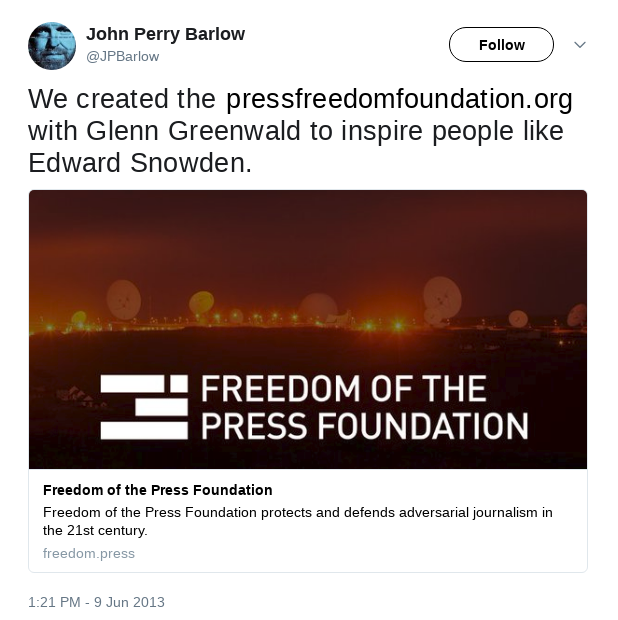
After few months of publishing the above mentioned article, one government
employee was moved by the words, and contacted FPF board members (through
Micah Lee). Later when his name become public,
Barlow posted the following tweet.
Next, Edward Snowden himself came in as the 4th speaker in the panel. He told a
story which is not publicized much. He went back to his days in NSA where even
though he was high school drop out, he had a high salary and very comfortable
life. As he gained access to highly classified information, he realized that
something was not right.
I realized what was legal, was not necessarily what was moral. I realized
what is being made public, was not the same of what was true. -- Edward
Snowden.

He talked about how EFF and JPB’s work gave direction of many decisions of his
life. Snowden read Barlow’s A Declaration of the Independence of
Cyberspace and perhaps that was
the first seed of radicalization in his life. How Barlow choose people over
living a very happy and easy life, shows his alliance with us, the common
people of the world.
After the first panel of speakers, Cory again took the stage to talk about
privacy and Internet. He spoke about why building technology which are safe for
world is important in this time of the history.
After a break of few minutes, the next panel of speakers came up on the stage,
the panel had Shari Steele, John Gilmore, Steven Levy, Joi Ito.

Shari was the first speaker in this group. While started talking about the
initial days of joining EFF, she mentioned how even without knowing about JPB
before, only one meeting converted Shari into a groupie. Describing the first
big legal fight of EFF, and how JPB wrote A Declaration of the Independence of
Cyberspace during that time. She chose a quote from the same:
We are creating a world where anyone, anywhere may express his or her beliefs,
no matter how singular, without fear of being coerced into silence or
conformity.
Later, John Gilmore pointed out a few quotes from JPB on LSD and how the
American society tries to control everything. John explained why he thinks
Barlow’s ideas were correct when it comes to psychedelic drugs and the effects
on human brains. He mentioned how JPB cautioned us about distinguishing the
data, information and the experience, in ways that are often forgotten today.
Next, Steven Levy kept skipping many different stories, choosing to focus on
how amazingly Barlow decided to express his ideas. The many articles JPB wrote,
helped to transform the view of web in our minds. Steven chose a quote from
JPB’s biography (which will be published in June) to share with us:
If people code out for eight minutes like I did and then come back, they
usually do so as a different person than the one who left. But I guess my brain
doesn’t use all that much oxygen because I appeared to be the same guy, at
least from the inside. For eight minutes, however, I had not just been
gratefully dead, I had been plain, flat out, ordinary dead. It was then I
decided the time had finally come for me to begin working on my book. Looking
for a ghost writer was not really the issue. At the time, my main concern was
to not be a ghost before the book itself was done.
I think Steven Levy chose the right words to describe Barlow in the last
sentence of his talk:
Reading that book, makes me think that how much we are going to miss Barlow’s
voice in this scary time for tech when our consensual hallucination is looking
more and more like a bad trip.
When you talk to Dalai Lama, just like when you talk to John Perry Barlow,
there is a deep sense of humor that comes from knowing how f***** up the world
is, how unjust the world is, how terrible it is, but still being so connected
to true nature, that it is so funny. -- Joi Ito
Joi mentioned that Barlow not only gave a direction to us by writing the
declaration of the independence of cyberspace, but, he also created different
organizations to make sure that we start moving that direction.
Amelia Barlow was the last speaker of the day. She went through the 25
Principles of Adult Behavior.
The day ended with a marching order from Cory Doctorow. He asked everyone to
talk more about the Internet and technologies and how they are affecting our
lives. If we think that everyone can understand the problems, that will be a
very false hope. Most people still don’t think much about freedom and how the
people in power control our lives using the same technologies we think are
amazing. Talking to more people and helping them to understand the problem is a
good start to the path of having a better future. And John Perry Barlow showed
us how to walk on that path with his extraordinary life and willfulness of
creating special bonds with everyone around him.
I want to specially thank the Internet Archive for
hosting the event and allowing the people like uswe who are in the cyberspace to
actually get the feeling of being in the room with everyone else.
Recording of the event
Header image copyright: EFF