SecureDrop QA workflow and how to improve it?
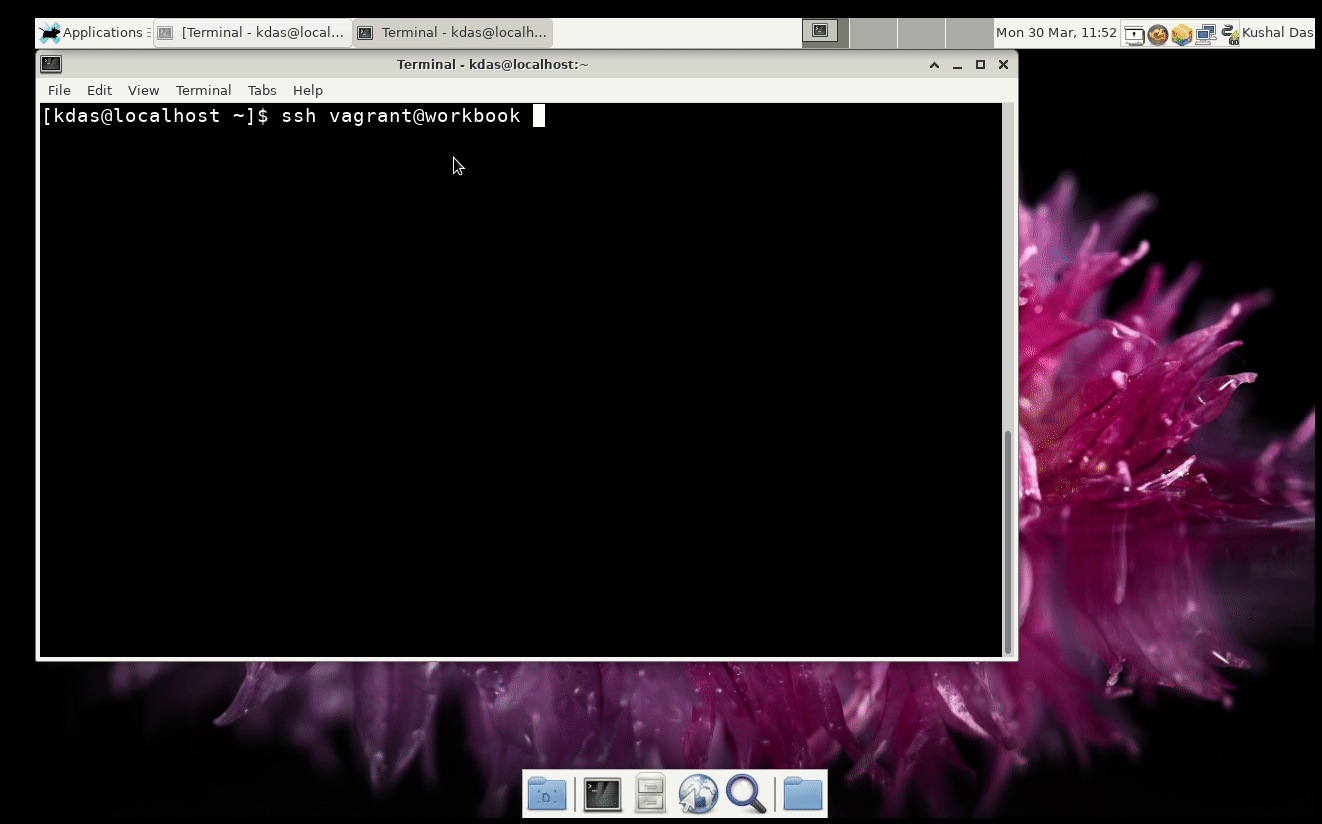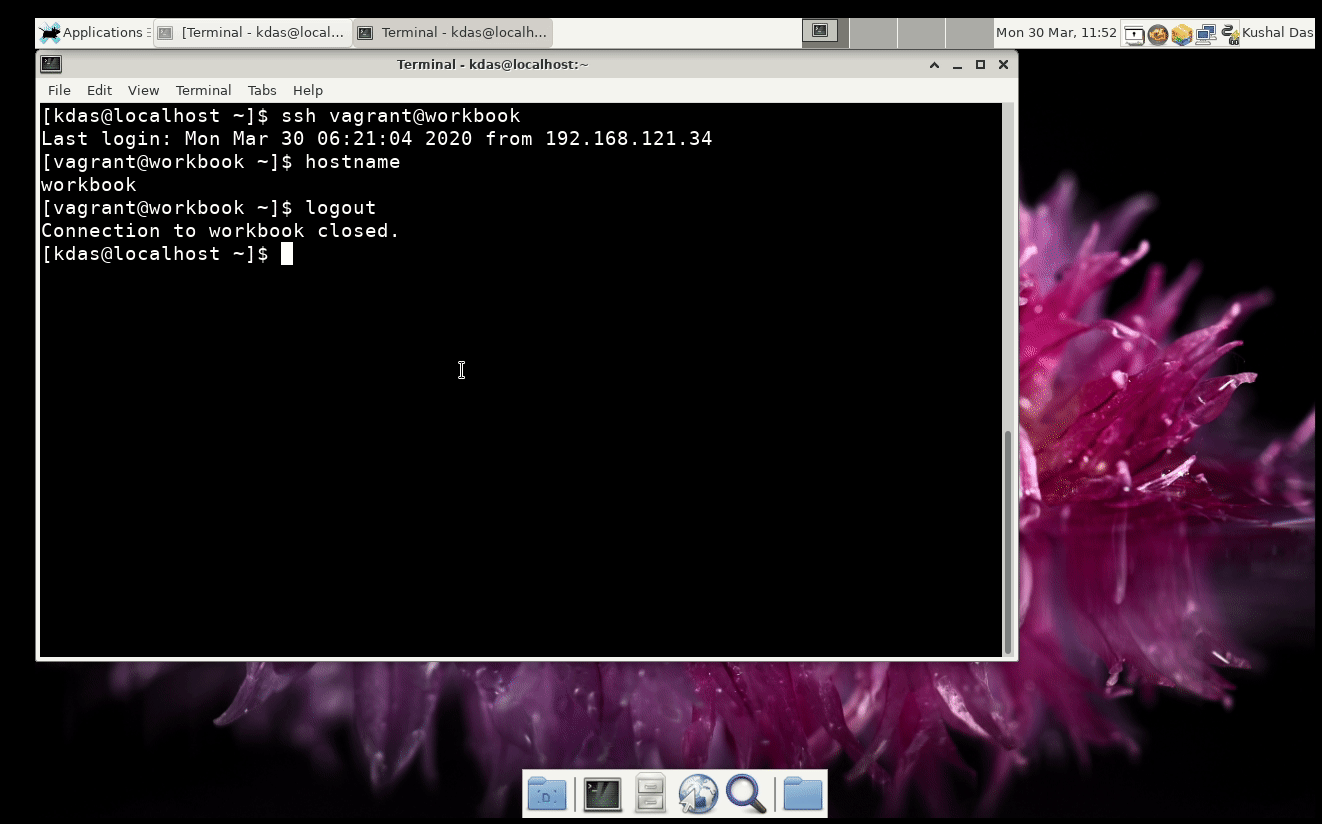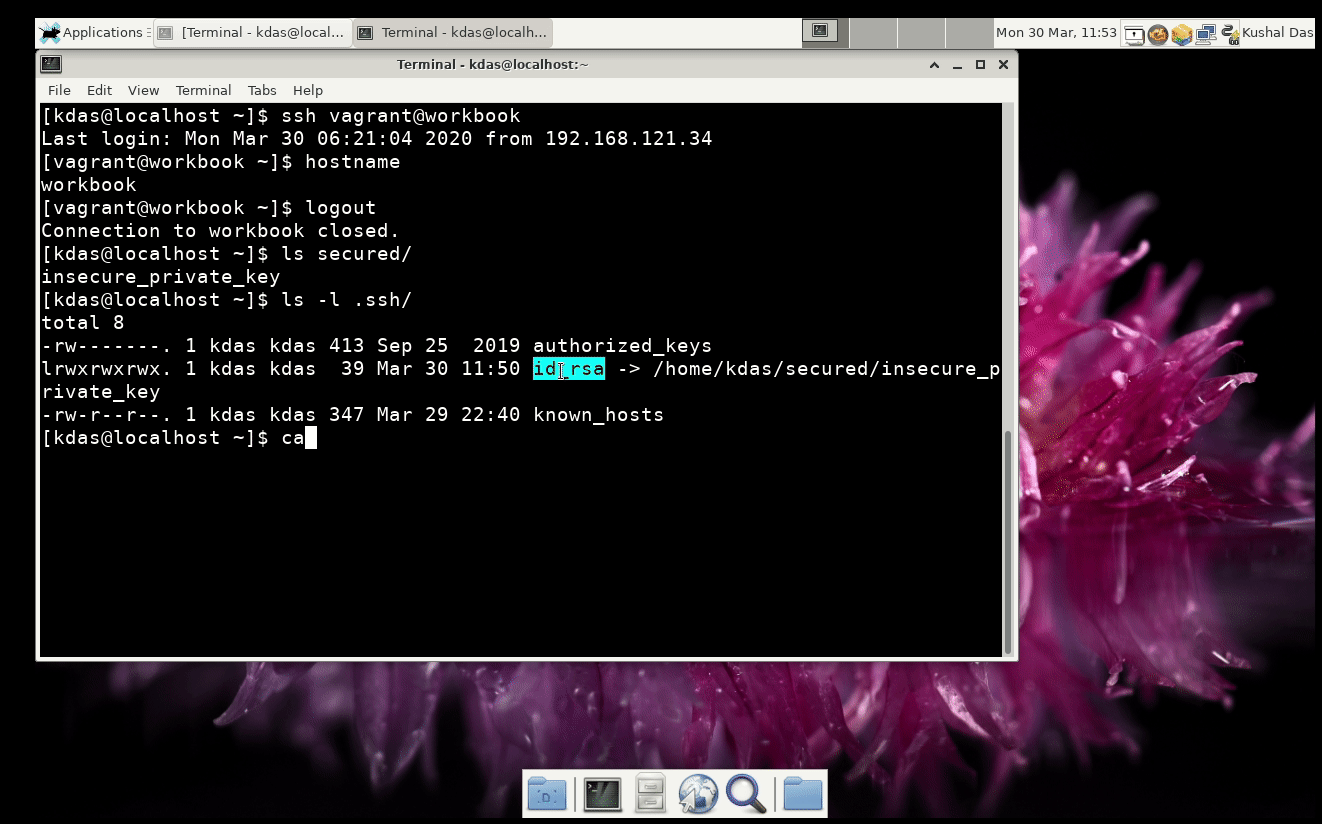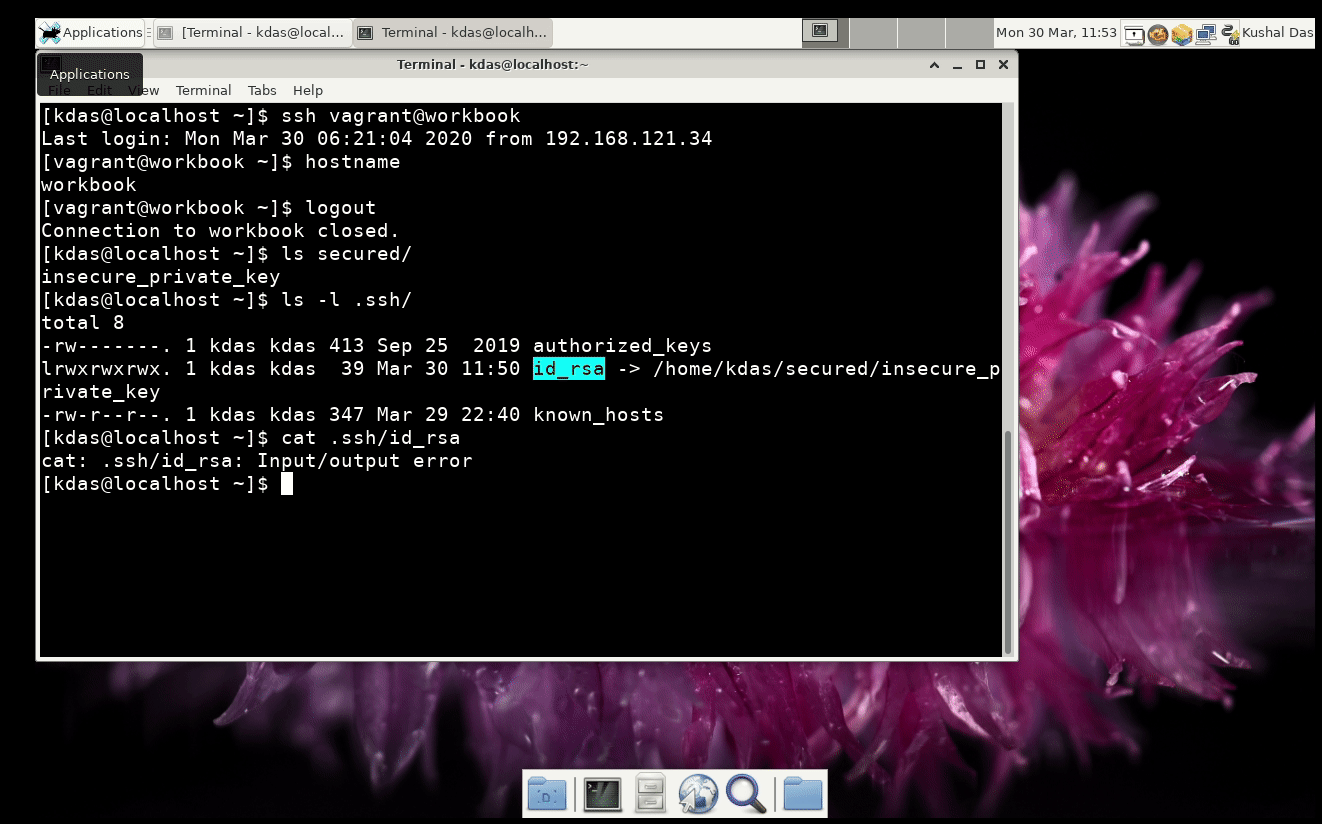
Right now, we are in the QA period for the SecureDrop 1.6.0 release. SecureDrop is an open-source whistleblower submission system that media organisations and NGOs can install to securely accept documents from anonymous sources. It was originally created by the late Aaron Swartz and is now managed by Freedom of the Press Foundation.
In this blog post I am going to explain how we do the QA for the release. I hope you can suggest some ways to improve the steps and make it better.
A few properties of SecureDrop to keep in mind during QA
- It is a complex web application that gets auto-updated via the Debian package on the servers running around the world.
- Security has the highest priority.
- We (the developers) do not have any access to those servers.
- Most of the servers are maintained by the system administrator from the news organization who very little time to manage and many times no Linux skill set.
- It is actually 2 servers per installation.
- Officially supported hardware list contains a few different generations of Intel NUCs, and Mac Minis.
- We also provide our own kernel package for these systems.
Test plan
The test plan for each release is tracked on the wiki and linked from the release ticket. Each time, we have the following categories of test cases:
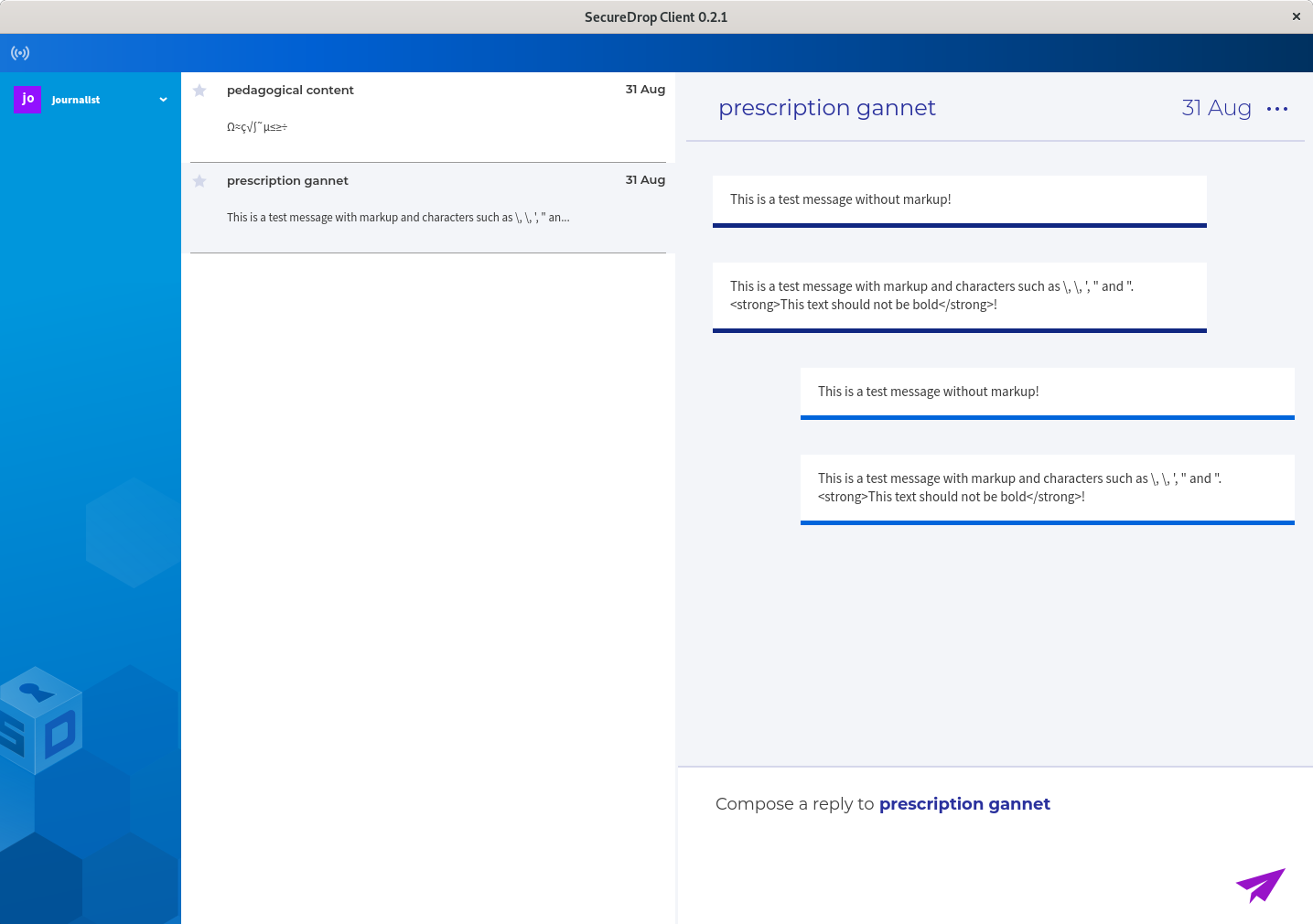
- Application Acceptance Testing (related to general application usage)
- Basic Tails testing (for the tails updated GUI tool)
- Release specific changes for each release (detailed tests for new/updated features/fixes)
- Preflight check (for the release process itself)
We also have a private QA matrix, where we track things for each supported hardware (for update and new install) in a spreadsheet so that it becomes easier to understand if any basic test (say if the system is booting) is failing.
Please go through the test plan and the workflow. If you have any suggestions, you toot/tweet or email me. Your input is precious to make SecureDrop a better and safer tool for whistleblowers around the world.